Evolution of my link roundups
As you may have noticed, I'm a fan of link compilation digests.
However, compiling them was quite the work for me. I always found interesting links during the week, then had to reserve an hour in the weekend to prepare the blogpost, which sometimes I did not had.
Furthermore, this format was flooding my blog with link roundups, which is not very user friendly for somebody who stumbles upon my front page.
I needed something better in two ways. First, the link publication has to be on the spot. Adding them to a list, then editing a post was not cutting it. Second, the links need to be their own section, independent from the rest of blog posts.
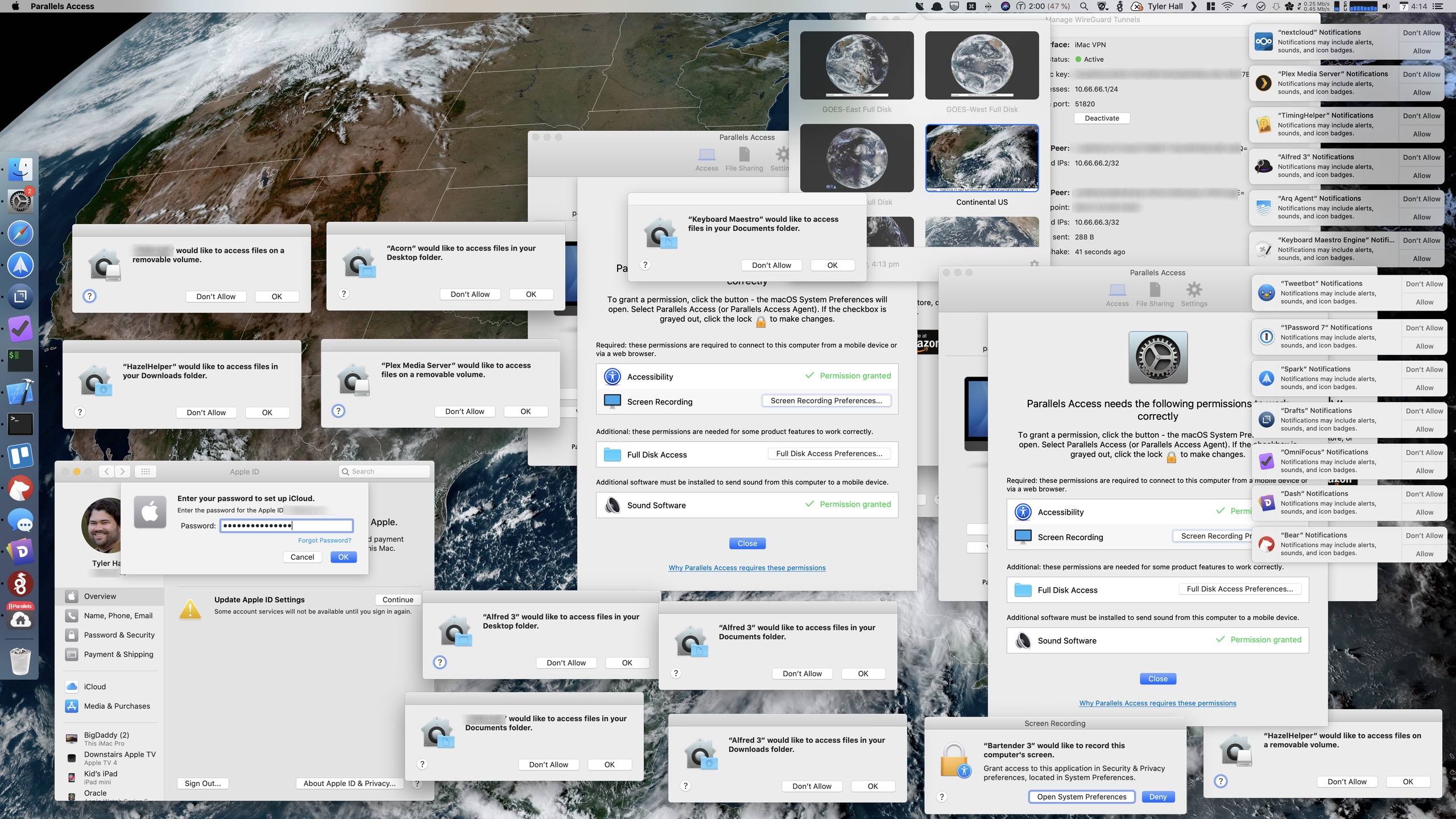
Fortunately, one of my link sources had the solution in front of me. The idea behind it is very simple and I got inspired by waxy's implementation. A box with links in the front page, and a special page only with links.
So this weekend project has been a very nice 1-line patch to bashblog, a bit of messing with postfix to parse links received to a special inbox, and some glue on top of it. I'm happy with the result!
The links index page is very crude right now. There is no CSS, and no feed available, but that will come soon. Meanwhile, feel free to bookmark it and visit it sometime!
Links for 2020-02-09
🐲 For Tolkien fans 🔗
The Tolkien Meta-FAQ (RH, via usenet)
Usenet FAQs used to be a great source of information. I recently found the Tolkien Meta-FAQ and it is absolutely amazing.
🎨 Mario Paint tunes 🔗
Meet the musicians who compose in Mario Paint (5 min, via waxy)
Delightfully retro.
PS: There is a Mario Paint subreddit!
💣 Android remote code execution via Bluetooth 🔗
Critical Bluetooth Vulnerability in Android (CVE-2020-0022) (1 min, via @[email protected])
On Android 8.0 to 9.0, a remote attacker within proximity can silently execute arbitrary code [...] as long as Bluetooth is enabled. No user interaction is required.
I wonder if there are exploits in the wild already. Walking around a big city infecting all phones in a 10-foot radius.
🤯 40 concepts for understanding the world 🔗
In 40 tweets I will describe 40 powerful concepts for understanding the world (5 min, via @paulg)
This thread is worth reading. It's better than most popular books about ideas, and much shorter.
📒 What they don't teach you in CS classes 🔗
The Missing Semester of Your CS Education (RH, via lobste.rs)
Over the years, we have seen that many students have limited knowledge of the tools available to them.
Common examples include holding the down arrow key for 30 seconds to scroll to the bottom of a large file in Vim, or using the nuclear approach to fix a Git repository (https://xkcd.com/1597/)
This is one of the best resources I have ever linked to.
You must learn these skills.
(Self plug: my own UNIX tools workshop slides)
🚂 Upscaling a 1896 film with AI 🔗
Someone used neural networks to upscale a famous 1896 video to 4k quality (5 min, via HN)
We already had this capability. Only that it required an enormous effort by experienced video editors.
In a few years movies will be created just by feeding a script to an AI.
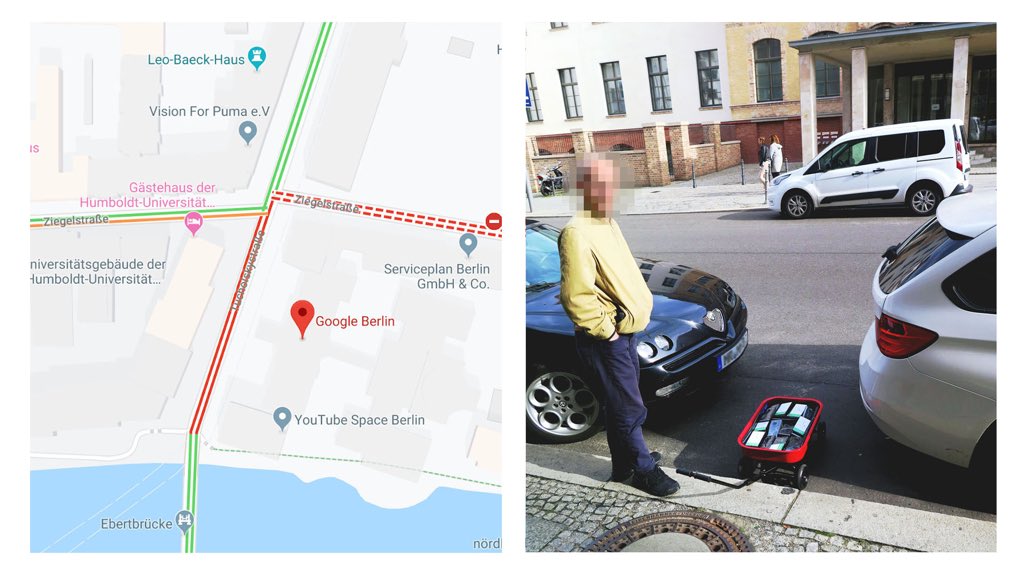
🚗 Fake GMaps traffic jam 🔗
Google Maps Hacks (5 min, via @simon_deliver)
99 smartphones are transported in a handcart to generate virtual traffic jam in Google Maps. Through this activity, it is possible to turn a green street red which has an impact in the physical world by navigating cars on another route!
Devilishly genius!
Tags: roundup
Links for 2020-02-02
💣 Remote exploit in OpenSMTPd 🔗
OpenSMTPD advisory dissected (5 min, via)
The author of OpenSMTPd does a good post-mortem of the catastrophic bug that has left a remote exploit available for three years and a half.
We can’t prevent human mistakes, they will happen because tools won’t help spot that a human-described logic is flawed. What we need is to make changes so that OpenSMTPD becomes more resistant to human errors. In other words, we need safe-guards that are not dependant on sanity checks and input, we need safe-guards that will guarantee that even if OpenSMTPD lets completely untrusted input pass through, this will have the most limited consequences... then we ensure that it doesn’t let untrusted input pass through.
Agreed. There is no such thing as bug-free code.
🖥 CacheOut, another Intel CPU vulnerability 🔗
CacheOut, Leaking Data on Intel CPUs via Cache Evictions (5 min, via)
Every single one of these would be a scandal. Now, we've gotten used to it. Shame on Intel.
👴 UNIX lore 🔗
The Unix Heritage Society (RH, via)
Great resource to learn more about UNIX history.
Make sure to browse their wiki
💉 Antivirus selling user data 🔗
Leaked Documents Expose the Secretive Market for Your Web Browsing Data (1 min, via)
An Avast antivirus subsidiary sells 'Every search. Every click. Every buy. On every site.' Its clients have included Home Depot, Google, Microsoft, Pepsi, and McKinsey.
How ironic.
🎨 Oldschool web design trends 🔗
Dark Ages of The Web (2 min, via) is a visual trip through old web design trends.
It contains, of course:
- Tables
- Animated gifs
- The Web 2.0
- Flash
- The "Home Page"
and more
🏴☠️ Whatsapp hack for Jeff Bezos 🔗
Technical Report of the Bezos Phone Hack (20 min, pdf, via)
Besides the actual forensics of the hack, which are not very in depth, this report provides an interesting insight into the tools and environments that real security firms use to study malware. It seems that Cellebrite's software is very popular.
Be sure to read the HN discussion, which seems to agree with my point: the forensic analysis was not very good, but the between-lines content is insightful.
🍎 Vintage Apple magazines 🔗
VintageApple, Information from the early Apple era (RH, via) is an archive of vintage Apple material, like magazines, books, pictures, and more.
Make sure to check this one out if you're a retro Apple fan.
👁 The Eye, another internet archive 🔗
I hope you already know about The Internet Archive, a non-profit effort to archive a lot of content on the Web. If you don't, contgratulations! Play with MS-DOS software in your browser, read free books and watch copyright-free movies
Then, check out The Eye. It's another non-profit project aimed at file archival, a bit more chaotic, which makes browsing through its pages a real archeology dig.
The-Eye is a non-profit, community driven platform dedicated to the archiving and long-term preservation of any and all data including but by no means limited to... websites, books, games, software, video, audio, other digital-obscura and ideas.
🕹 Starfox into Zelda 🔗
This amazing glitch puts Star Fox 64 ships in an unmodified Zelda cartridge (15 min, via)
The fact that these glitches can be run, and that there is people actively looking for them, makes me very happy.
Let's give due credit: Zfg1 on Twitch
Related link: Ocarina of Time glitches and code execution
Tags: roundup
Links for 2020-01-26: bash power and Windows nostalgia
📝 How to write good bash 🔗
Anybody can write good bash (with a little effort) (5 min, via) provides some basic techniques to make your scripts more robust.
The article already mentions this, but I'll reiterate: use shellcheck
⌨️ More bash tricks 🔗
THC's favourite Tips, Tricks & Hacks (Cheat Sheet) (5 min) is a nice compilation of shell/unix tricks and tools.
If you liked these, make sure to read my own compilation of UNIX tricks
🌍 Bash web server 🔗
bashweb, A tiny web server that serves static files (1 min) is the perfect companion to my own bashblog, I guess?
✏️ Vanilla vim is nicer than you think 🔗
How to Do 90% of What Plugins Do (With Just Vim) (1 hr, video)
Vim is big; so big that it does some very useful things that are often overlooked. Plugins can buy us a lot of functionality, but they can add a lot of burden in the form of dependency complexity. In this talk, we'll explore some of the tradeoffs we can make between plugins and "vanilla" Vim features that achieve similar results, including:
- autocomplete (VimAwesome, YouCompleteMe)
- file jumping (FuzzyFinder, Ctrl-P)
- visual filesystem navigation (NERDTree)
- build integration
- snippets
An informative, practical and enjoyable talk.
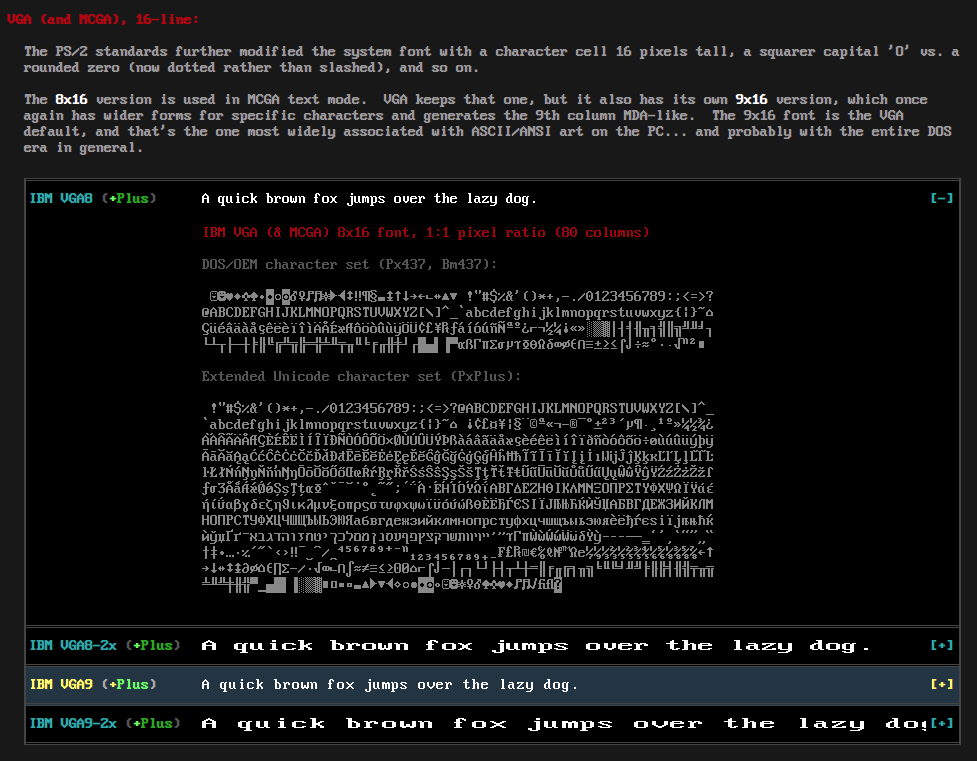
🔠 Oldschool fonts 🔗
The Ultimate Oldschool PC Font Pack (5 min, via) is exactly what the title says.
It contains my favorite font of all time, IBM VGA8, the one I use in all my terminals, which I'm looking at while I write this blogpost.
🔐 How to use security usb keys 🔗
Getting started with security keys (15 min, via)
This is the definitive guide on how to set up security keys. It's full of resources, news, and specific gadgets that you can use.
The site is beautiful too, be sure to check it out!
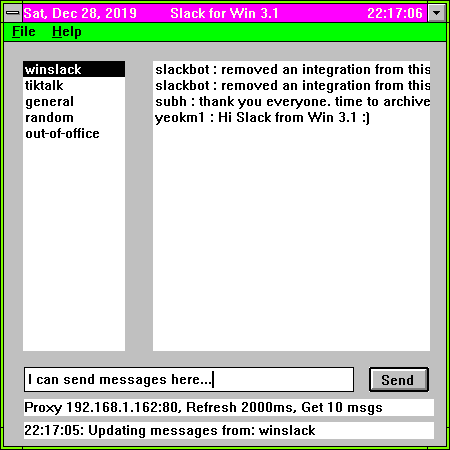
💬 Developing Slack for win31 🔗
Building a new Win 3.1 app in 2019 (5 min)
This is so delightful. Even the win31 colorscheme brings great memories.
☑️ Why the Windows 95 UI was so great 🔗
Not everything was perfect in 1995, but I think we've lost something on the way (1 min, tweetstorm, via)
I wholeheartedly agree with Tuomas here.
I despise flat design for software. It is confusing, ugly, and throws out the window (pun intended) what we learned in the last 30 years of UI design.
💀 Windows 7 EOL 🔗
Windows 7 support ended on January 14, 2020 (1 min, via)
While I hate Windows in general, and not only from a philosophical point of view but rather because they're terrible tools, what Microsoft has done with Windows 10 is disgusting.
I've had to pay for Windows 10 copies for my company, and in return the system is slow, spies on you, and has ads on the Start menu.
Windows 7 didn't have that, so that's something. Not that it was a good experience, either
Sorry for the rant. I have nothing interesting to contribute regarding the actual link. I just couldn't pass on the opportunity to hate on modern Windows.
👴🏼 Appreciating resilient software 🔗
Writing Software to Last 50 Years
(5 min,
via)
is a short article that uses grep as an example of good, lasting software.
The author analyzes some of the reasons that make good tech.
Thanks to a comment by andyc I've learned about the Lindy Effect: the longer some tech has been available, the longer you expect it will continue being available in the future.
⛓ Cloudflare, the Gatekeeper 🔗
Cloudflare is turning off the internet for me (1 min, via)
I could not finish one of these roundups without your weekly reminder that the centralization of the internet is a scary thing and we all have the responsibility to fight against it.
🏴☠️ Support the Indie Web 🔗
The IndieWeb, a people-focused alternative to the "corporate web" (RH)
What can we do to push against a total centralization of the Internet by a dozen of companies?
Subscribe to independent RSS feeds, do not use Cloudflare unless strictly necessary, move your conent out of the mainstream platforms, use federated networks, etc.
Do not play their game.
Tags: roundup
Links for 2019-12-08
💻 Hack your Thinkpad 🔗
My personal fight against the modern laptop (45 min, video, via)
In this talk, I will take you through the tools and techniques I used to reverse engineer the keyboard controller in my Thinkpad laptop and re-flash it with custom firmware.
Thinkpad keyboards, never such a niche topic has generated so much debate

💥 Fight AMP 🔗
How to fight back against Google AMP as a web user and a web developer (5 min, via)
The actual contents of the article are not that interesting —don't use Google, don't use Chrome, speed up your website— but the topic is, and the HN discussion is quite insightful
HN user soyyo comments
For publishers, amp is about trying to top the results on google search and capture traffic, it's their only motivation to publish their content using amp, and the only metric they look in order to evaluate the results.
🐲 AI-generated text adventure 🔗
AI Dungeon 2 – AI-generated text adventure built with 1.5B param GPT-2 (RH, via)
Imagine an infinitely generated world that you could explore endlessly, continually finding entirely new content and adventures. What if you could also choose any action you can think of instead of being limited by the imagination of the developers who created the game?
If you love text adventures (you should) and you're ready to be mildly amused by the fact that an AI is generating the game (you should), go ahead and give it a go.
📲 2/3 of your battery is used to move data around 🔗
In mobile, 62.7% of energy is spent on data movement (15 min, PDF, via)
The title may suggest that we're talking about the antennas, but it's focused on moving data from memory, and suggests designing new RAM systems with specific instructions for copying and zeroing data.
A bit long, but very interesting.
📹 30 -> 60 fps using AI 🔗
Turning animations to 60fps using AI! (4 min, video, via)
Depth-Aware Video Frame Interpolation [DAIN] is a project that let you interpolate frames using an advanced AI.
Just watch this video:
🐇 A first look into Plan 9 🔗
Plan 9: Not dead, Just Resting, by Ori Bernstein (1h, video, via) and How I Switched To Plan 9
Plan 9 is an experimental OS that takes some UNIX principles to the extreme.
Plan 9 from Bell Labs is a research system developed at Bell Labs starting in the late 1980s. Its original designers and authors were Ken Thompson, Rob Pike, Dave Presotto, and Phil Winterbottom.
Plan 9 demonstrates a new and often cleaner way to solve most systems problems. The system as a whole is likely to feel tantalizingly familiar to Unix users but at the same time quite foreign.
In Plan 9, each process has its own mutable name space. A process may rearrange, add to, and remove from its own name space without affecting the name spaces of unrelated processes. Included in the name space mutations is the ability to mount a connection to a file server speaking 9P, a simple file protocol. The connection may be a network connection, a pipe, or any other file descriptor open for reading and writing with a 9P server on the other end.
It is not well suited for most people's daily needs, but it is very interesting both from a research and from a hobbyist point of view.
Think about it as "Plan 9 is to OpenBSD what OpenBSD is to Linux."
Make sure to check out the links above and fall into the Plan 9 rabbit hole.
🐍 Malicious Python libraries 🔗
Two malicious Python libraries caught stealing SSH and GPG keys (1 min, via)
The first is "python3-dateutil," which imitated the popular "dateutil" library. The second is "jeIlyfish" (the first L is an I), which mimicked the "jellyfish" library.
Well, another attack to add to the books. Let's keep vigilant when including non-vetoed libraries in our code.
🧮 Vim-like tools 🔗
Big Pile of Vim-like (RH, via)
E-mail clients, file managers, browsers, music players... a bunch of software designed after some vim feature.
If you're a vim fan this is a must read!
🍎 What it's like to sell your company to Steve Jobs 🔗
Andy Miller | Sold 1st Co. For $275m, Future of Esports (1 hour, video)
What a fascinating story! Andy Miller explains how he sold his company to Apple, with plenty of anecdotes.
A very rare window inside the mind of Steve Jobs: how he lowballed the exit price with a veiled threat, how he pushed people over acceptable limits to make the most out of theirselves, and how Andy stole Jobs' laptop by mistake on what probably was the worst day of his life.
If you're a Jobs fan, this piece is one of a kind. Watch the video, or convert it to mp3 and listen to it as a podcast.
🌌 The end of the universe 🔗
TIMELAPSE OF THE FUTURE: A Journey to the End of Time (30 min, video)
Do you wonder how the universe will end? This excellently produced video explains how the stars will die, and then black holes, and then photons, until there is nothing in the universe, and that nothing stays forever.
A beautiful, moving piece, very informative, that helps put things into perspective.
📡 How radar works 🔗
How Radar Works (15 min, via)
The author makes great effort into explaining how radar works, both from a theoretical point of view, and also with formulas.
I must admit that the math is a bit out of my comfort zone, but I recommend that you read it and at least try to understand the basic concepts. It's worth it.
Tags: roundup
Links for 2019-12-01
Ocarina of Time glitches and code execution 🔗
Arbitrary Code Execution in Ocarina of Time (30 min, video via)
I find these kinds of glitches fascinating. See for yourself!
Online tools for pet projects 🔗
Software Tools for Hobby-Scale Projects (RH, via)
Below is a list of useful tools I’ve come in contact with over the years.
- They cost less than a coffee or are free.
- They can be learned quickly.
- They allow you to accomplish a single task in a short timeframe (such as a Sunday afternoon)
- They are less focused on the needs of long term projects (scalability, speed, etc.) and more focused on ease of use and prototyping speed.
Rick Carlino has compiled a very nice list of online tools, such as mobile push notifications, VPS and DB hosting.
I have to admit that many of these were new for me, so it's definitely not a rehash of the usual links. Great list!
BBS: The documentary 🔗
BBS The Documentary (5 hours split in 8 videos)
In the Summer of 2001, Jason Scott, a computer historian (and proprietor of the textfiles.com history site) wondered if anyone had made a film about these BBSes. They hadn't, so he decided he would.
Fascinating. I've just put the videos in my watch queue.
Trying out NomadBSD 🔗
NomadBSD | Installation & First Impressions (20 min, video via)
For some reason, this is the first time I've heard about NomadBSD. It's a "portable" version of FreeBSD, to be run from a USB drive.
Anybody remember Knoppix? The first popular Linux distro that could be run from a CD. It contributed to hardware discovery on boot, and thanks in part to their efforts, Linux hardware setup did a huge leap forward.
Hope that NomadBSD can do that for FreeBSD, which already has reat hardware support, albeit limited, but its defaults are not so great.
Darwin OS 🔗
A Look at PureDarwin - an OS based on the open source core of macOS (5 min, via) provides some background, history and status of the PureDarwin project, a 100% free software OS built on top of the Darwin (macOS) kernel
Metadata leak with SSH keys 🔗
Public SSH keys can leak your private infrastructure (5 min, via)
You don't need a private key to validate if a server allows access from a particular public/private key combination. That is, by having access to a public key, you can check if a server allows access for the specified public key and a username pair
This is a known issue. Filippo Valsorda posted a related proof of concept in 2015.
My SSH server knows who you are (5 min, 2015, via)
Did you know that ssh sends all your public keys to any server it tries to authenticate to?
If this metadata disclosure is a problem for you, the solution is very simple.
- Configure your ssh to NOT send any pubkey to unknown hosts
- Create a new ssh keypair for every new host you want to connect to (see link above)
Instructions here, courtesy of HN user chrisfosterelli.
Advent of Code 2019 🔗
Advent of Code 2019 (RH, via)
Advent of Code is a code advent calendar. Each day unlocks a new programming challenge. You score points by completing the challenges quickly
A few years ago I solved some of their challenges and they're really fun.
Be careful! As lobste.rs user narimiran says:
Don't be fooled: You will not just solve tasks and be over with it. There will be tasks that you'll think about all day and you won't be able to think about anything else. And you'll love it :)
Yup. The RH tag is warranted here.
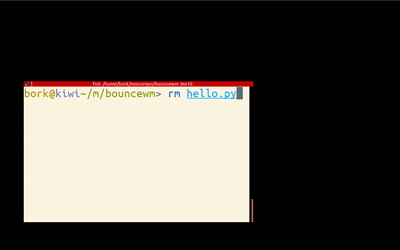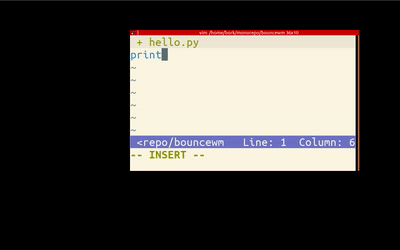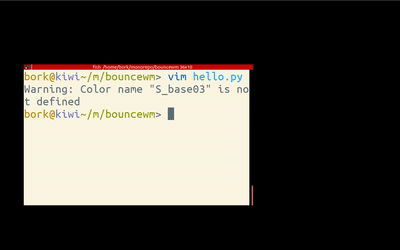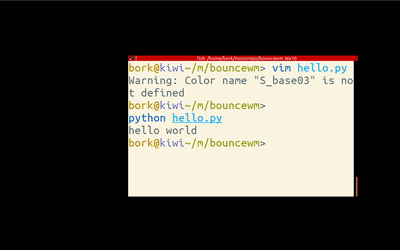
Writing a simple window manager 🔗
Challenge: Write a bouncy window manager (RH, via)
Julia Evans plays with tinywm and her enthusiasm is contagious.
Though I use the admittedly weird dwm as my WM, and I've hacked some of its code, I've never considered to write my own WM, or even realized how easy it is.
Give it a try: tinywm is just 50 lines of very readable C.
On messaging services
Choosing the Right Messenger (10 min, via) is not a list of messenger services, but rather a thoughtful discussion on privacy tradeoffs: encryption, metadata, sign up process, source code availability, etc.
I highly recommend that you read the article if you're interested in learning more context on why some messengers are more secure/private than others.
The end of IPv4 🔗
The RIPE NCC has run out of IPv4 Addresses (1 min)
Our announcement will not come as a surprise for network operators - IPv4 run-out has long been anticipated and planned for by the RIPE community.
Let's see if we can quickly move to an ipv6 world -- my mail server will surely benefit from an untainted ip.
The Twitter Purge 🔗
Twitter prepares for huge cull of inactive users (1 min) and Twitter account deletions on 'pause' after outcry (1 min)
Twitter is (was) planning to remove inactive accounts. Even though it would free their handles for new users, apparently the main reason is that those users didn't accept the new terms of service.
There are many interesting angles, but for once, I have to stay on Twitter's side.
However, they should have provided an option to archive these old accounts; after all, users accepted that their content was to be owned and distributed by Twitter. Even if they can't log in, or their account is deleted, Twitter could have stored the content somewhere visible.
Tags: roundup
Links for 2019-11-24
Some SSD encryption is not secure 🔗
How secure is hardware disk encryption? (1 min, Twitter thread)
Dan Luu links to a paper by Mejier C et al., titled Self-encrypting deception: weaknesses in the encryption of solid state drives
In a nutshell:
We have analyzed the hardware full-disk encryption of several solid state drives (SSDs) by reverse engineering their firmware.
We found that many models using hardware encryption have critical security weaknesses due to specification, design, and implementation issues [that] allow for complete recovery of the data without knowledge of any secret (such as the password).
To make matters worse:
BitLocker, the encryption software built into Microsoft Windows will rely exclusively on hardware full-disk encryption if the SSD advertises support for it. Thus, for these drives, data protected by BitLocker is also compromised.
TL;DR:
Roughly 60% of the market [is affected] currently one should not rely solely on hardware encryption offered by SSDs and users should take additional measures to protect their data.
This is really, really bad.
Download old Linux distros 🔗
Linux Distros (RH) is an archive of old Linux ISOs that you can install on a virtual machine or similar.
Every entry has screenshots, making it a very nice resource to browse even if you don't commit to testing the distros.
Designing a modern text editor 🔗
Neovim and the state of text editor art in 2019 (15 min, pdf, via)
I never thought that a text editor could be such a complex and inspiring software product!
There is a video of the talk (50 min) in case you want more context than the bare slides.
GIF like it's 1999 🔗
The 88x31 GIF Collection (RH, via)
A collection of 2680 classic 88x31 buttons from the 1990's, 2000's, and today in GIF format.



Windows 95 UI 🔗
Designing Windows 95's User Interface (15 min, via)
Three years ago I came across an interesting paper written up by a Microsoft employee, Kent Sullivan, on the process and findings of designing the new user interface for Windows 95.
The website archives Sullivan's paper The Windows 95 User Interface: A Case Study in Usability Engineering, a very interesting text on easly GUI usability, along with screenshots comparing 3.1 and 95 interface which will put a smile on your face.
OpenBSD review 🔗
OpenBSD in 2019 (10 min, via)
I've written similar texts about OpenBSD twice, and I like reading other people's opinions.
There is a pattern here: somebody is angry with some Linux drama, tries OpenBSD, likes it, but for some reason can't use it as a daily driver.
Check it out if you are still unsure about its strengths and weaknesses compared to Linux and/or other BSDs.
There is a very good Reddit discussion about this post.
A p2p web browser 🔗
Beaker (2 min, via) is an experimental web browser which supports dat://, a modern p2p protocol.
I really like these experiments. I'm not sure if it will take off, but re-decentralizing the web is a great cause.
ASCII art game 🔗
ASCIIDENT (RH, via) is an "Open-world sci-fi game with a design completely made by text characters."
After trying the demo, I'd define it as a platform game like Duke Nukum, with a crafting element, and the ASCII novelty which makes it quite nice
I have to admit I'm tempted to buy the game. To my wishlist it goes...
Save .org 🔗
Save .ORG (2 min) is a plea to stop the sale of .org domains control to an equity firm.
Worth a read, check out the original signers. Wikimedia, the FSF, the EFF, the Internet Archive... this is not your typical bullshit change.org petition.
Check out the HN discussion with some alleged ex-ICANN members.
AI is not Terminators 🔗
AI today and tomorrow is mostly about curve fitting, not intelligence (5 min, via)
Some people cricize AI because we don't have terminators yet.
On the other hand, there is a lot of AI snake oil
The truth is: people in the field understand that we are harnessing the power of advanced curve fitting, not Hard AI.
It's our job to make journalists and the general public understand it, too.
Pornhub as a bastion of freedom 🔗
Banned from Youtube, Chinese propagandists are using Pornhub to publish anti-Hong Kong videos (1 min)
We truly live in the Craziest Timeline
RSS bridge 🔗
RSS bridge (2 min, via) is a connector that generates RSS feeds for sites that don't have one (e.g. Instagram, Twitter, Bandcamp...)
Last week I linked to Fraidycat, a similar concept.
I definitely need to set some time aside and check out both tools. I'd love a way to transform friends posts into an RSS feed.
Altair BASIC source code available 🔗
Micro-Soft Altair BASIC 3.2 source (RH, via)
After clicking on the link above, since this is the last one in the roundup, now go watch Pirates of Silicon Valley
Enjoy!
Tags: roundup
Links for 2019-11-17
PeerTube 2.0 released 🔗
PeerTube has worked twice as hard to free your videos from YouTube! (5 min, via)
PeerTube is a decentralized alternative to Youtube. Essentially, you can have your own Youtube-like website, with the added bonus that video traffic is distributed among viewers using p2p techniques.
PeerTube is to YouTube what Mastodon is to Twitter, but with an interesting benefit: you don't need to have your friends using it to enjoy the tool. If a cool video is on PeerTube, you can just go and watch it.
Gaming on OpenBSD 🔗
OpenBSD gaming Peertube (RH, via) combines two interesting concepts: Peertube, already mentioned above, and OpenBSD gaming, whichs seems like an oxymoron.
The OpenBSD gaming community is bigger and more vocal than you'd expect, and they have started to do livestreams with their favorite games, some of which, you'd never expected.
Solène is one of the most active members, make sure to follow her on Mastodon.
Using AI to scam $250k 🔗
Scammers deepfake CEO's voice to talk underling into $243,000 transfer (5 min, via) and its related AI Clones Your Voice After Listening for 5 Seconds (RH, via)
We're moving into a very cyberpunk future where you can only trust when you use your five senses.
Carmack working on AI 🔗
Carmack's statement (1 min)
Starting this week, I'm moving to a "Consulting CTO" position with Oculus. [...] As for what I am going to be doing with the rest of my time: [...] I have sometimes wondered how I would fare with a problem where the solution really isn't in sight. I decided that I should give it a try before I get too old. I'm going to work on artificial general intelligence (AGI).
Let's see what one of the top minds alive can do to help advance AI.
No police in Mastodon 🔗
The account of the Assam Police has been suspend from this instance (5 min, Mastodon thread)
An interesting discussion about banning cops in Mastodon instances. This is a gray topic with no easy solution, so I'll share some replies from users:
cm_kropot (OP):
The account of the Assam Police has been suspend from this instance.
We decided that we will not welcome cops on this instance, and we encourage the rest of the fediverse to do the same.
Following multiple reports, we decided that it's more important that our community feels safe and in security, than to be a platform for official communication.
Charles mentions pros and cons:
I can't speak for the mods, but I suspect the issue is more that they don't want the presence of police to have a chilling effect on speech. Police are very often at the sharp end of structural violence in any country.
However, cancelling police accounts may create a false sense of security. The police can still read your posts. They can still subpoena your mods. However, at least they're preventing from stirring up trouble.
Alex shares his experiences:
my experience from moderating a forum globally with popular ravers in the 90s/00s is discouraging overt cops works in the short term but (unsurprisingly) they switch to detective methods to glean info, often co-operating with journalists and agencies (often across borders), and it was still up to "normal" users not to blatantly incriminate themselves.
OTOH US corporate socnets welcome cops as "free moderators" so officers get a sense of entitlement to these spaces..
Ravi arguments on the other side of the spectrum:
Banning their official account from an open network is not going to solve any of those problems in the least. They can carry on their more nefarious activities under cover if required anyway. This ban only serves to illustrate a knee jerk reaction, goes against fediverse practice where somebody is banned only for CoC violation and not on a feel or whim, goes against free speech and is opaque without any upfront policies on this. This is worse than banana republic.
Protonmail can read your emails 🔗
Bitcoin and Protonmail, the calling cards of the cryptoshit techbro (5 min, Mastodon thread)
Drew, who you may know as the creator of sourcehut, argues against the use of Bitcoin and Protonmail.
The thread goes back and forth with many people, myself included, asking why Protonmail is not secure as they claim.
After all, the explanation is simple. The only way to send e2e encrypted mail is to use a technology which is similar to PGP.
- I write a plaintext email to [email protected]
- My mail server connects to mail.protonmail.ch and writes the plaintext email to it
- mail.protonmail.ch now has the plaintext email
Q.E.D.
I feel kind of cheated by Protonmail, because they are claiming something which is just impossible to do technically.
A more thruthful claim would be: after sending your unencrypted mail to the recipient, we promise to delete it and only keep an encrypted copy. But they do have access to a plaintext copy at some point. The only exception, it seems, is for mail sent between Protonmail accounts.
If you want security, disable hyper-threading 🔗
Running on Intel? If you want security, disable hyper-threading, says Linux kernel maintainer (2 min, via)
Here is a summary:
MDS is where one program can read another program's data. That's a bad thing when you are running in a shared environment such as cloud computing, even between browser tabs [...] I see a slowdown of about 20 per cent. That's real. As kernel developers we fight for a 1 per cent, 2 per cent speed increase. Put these security things in, and we go back like a year in performance. [...] We are still fixing Spectre 1.0 issues [almost] two years later. [...] If you're not using a supported distro, or a stable long-term kernel, you have an insecure system. It's that simple. All those embedded devices out there, that are not updated, totally easy to break [...]
Go ahead and read the full article, it's not much longer, and paints a pretty depressing picture for current Intel users.
(If you prefer to run a faster system with no security, read this)
The SQL detective 🔗
sql-murder-mystery (RH, via) is a game where you have to solve a crime by writing SQL queries.
Fun, but this is not a five minute game. Prepare a whole afternoon if you want to solve it.
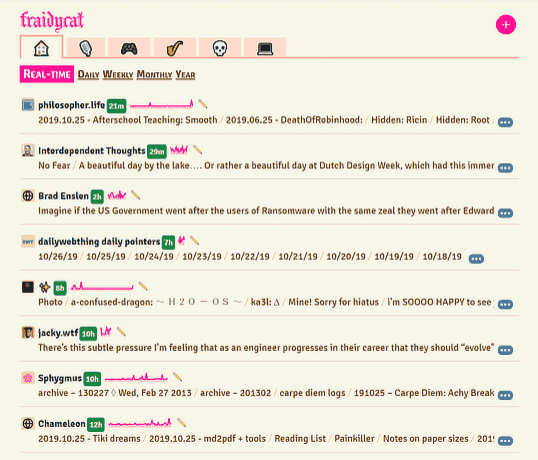
An aggregated "home feed" 🔗
is a browser extension for Firefox or Chrome that can be used to follow folks on a variety of platforms. But rather than showing you a traditional 'inbox' or 'feed' view of all the incoming posts, you are shown an overview of who is active and a brief summary of their activity.
and
Fraidycat attempts to dissolve the barriers between networks - each with their own seeming 'network effects' - and forms a personal network for you, a personal surveillance network, if you will, of the people you want to monitor.
I need to check this out in more depth. I would love to have something similar to this on my server, so I can access it from anywhere.
I want to follow people, not networks
You should have seen this 🔗
Greg Rutter's definitive list of the 99 things you should have already experienced on the internet unless you're a loser or old or something and his second list (RH, via)
- Charlie bit me
- Chocolate rain
- Mentos and diet coke
- Badger Badger Badger
- Play him off, keyboard cat
Stop reading this and watch the 198 videos NOW!
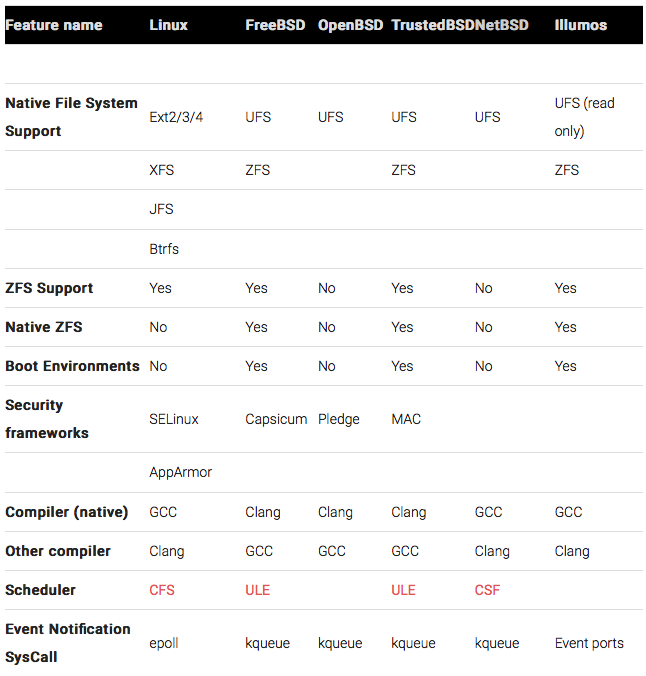
Feature comparison of UNIX flavors 🔗
Linux VS open source UNIX (30 min, via)
Is a very in-depth feature comparison of Linux and the BSDs, mostly at the kernel level. Not everybody's cup of tea, but make sure to at least check out the first table and the summary.
The Real UNIX 🔗
Will the real UNIX please stand up? (2 min, via) opens a discussion about UNIX roots and its impact in the 21st century.
At our level it's not worth worrying too much about which is the "real" UNIX, because all of these projects have benefitted greatly from the five decades of collective development. But it does raise an interesting question: what about the next five decades? Can a solution for timesharing on a 1960s minicomputer continue to adapt for the hardware and demands of mid-21st-century computing?
No more random phone searches in US airports 🔗
EFF statement (1 min, via)
In a major victory for privacy rights at the border, a federal court in Boston ruled today that suspicionless searches of travelers' electronic devices by federal agents at airports and other U.S. ports of entry are unconstitutional.
Some good news to wrap this roundup.
Tags: roundup
Links for 2019-11-10
Windows backwards compatibility is amazing 🔗
The Windows Update Marathon in a VM: From Windows 1.01 to XP (5 min, in German) and Upgrading Windows NT 3.51 to Windows 10 via 2000, XP, Vista, 8 and 8.1 in under a minute (1 min, video) both via
I can already hear the Windows 3.1, 95, 98 and XP startup sounds in my head. Can you?
Of course, nostalgia paints everything with rose colored glasses. Windows 3.1 was an amazing improvement over DOS. 95 brought real multitasking but it crashed constantly. 98 SE was the shit. XP started a bit wonky but with SP2 became a great OS. And anything that came later just sucks
Which brings us to...
Windows is not for OP 🔗
Back to windows after twenty years (2 min, via)
Apple's stubborn four-year refusal to fix the terminally broken butterfly keyboard design led me to a crazy experiment last week: Giving Windows a try for the first time in twenty years.
I have done this, for the same reasons (see link above)
However...
Anyway, I started this experiment on a Monday. I kept going all the way through Friday. Using the laptop as I would any other computer for the internet, and my new hobby of dealing with the stubbed toes of setting up a *nix development environment, but when I got to Saturday I just... gave up
Yup, seems about right.
Several top Spanish companies hit by ransomware 🔗
Everis and others hit by ransomware (2 min, Tweetstorm, in Spanish, via and discussion in English)
Two years ago, Telefonica, the Spanish telco, was hit by Wannacry, too
Ransomware is pretty scary. However, when you remember how viruses in the past just deleted your files, it makes you think. Do you prefer total destruction or a possibility of recovery through blackmail?
Remember:
- Check your backups
- Keep your OS always up to date
- Don't use Windows unless strictly necessary
Spain passes its own "PATRIOT Act" 🔗
Críptica analyzes the new Spanish Digital Act (2 min, Tweetstorm, in Spanish)
Yes, Spain has hit the tech news twice this week.
Well, it was a matter of time. Spain already had a law which allowed the Government to close websites without a court order, which is outrageous on itself and has recently been used already to silence political dissent.
Now, the Government will have power to cut communications infrastructure (i.e. cellphone signal, internet at the ISP level) in situations where national security is at risk (ok) but also to protect public order (not ok)
Since any protest can disrupt public order, this new mechanism can be used almost indiscriminately.
Note: This law has been tuned by an acting government, during the general elections campaign.
All issues of the now defunct Linux Journal 🔗
Linux Journal complete (PDF) collection (RH, via) is an archive of the recently discontinued Linux Journal, a veteran in the industry.
F
Web vs native 🔗
Apple Is Trying to Kill Web Technology (2 min, via) is a manifesto that defends web apps.
In my opinion, it is misleading because it blames Apple, not the Electron developers, who are at fault for accessing private APIs. That is another topic of discussion, but hey, isn't it ironic? If you develop a web app that accesses private APIs, maybe you would be better served by a... native app?
Regardless, there a few valid points:
Apple's control over its app ecosystem is a new type of monopoly that's hard to understand for lawmakers, and difficult for us to fight back against — because there simply isn't a way out of these restrictions when the company controls both the distribution method and the platform itself
But again, this has nothing to do with Electron using private APIs to try and suck less.
I hate Electron apps, in case you didn't notice. Sorry. Everybody has their own biases.
Bash toolchain 🔗
Library for bash utility methods and tools, Shell Script Library, Bash Automated Testing System and Bash Infinity, a modern boilerplate / framework / standard library for bash (RH, via)
You may know I'm a Bash fan, so these finds are like gold to me.
The moral of the story is: don't dismiss bash without analyzing your requirements first.
Know Thy Computer 🔗
There's No Such Thing as Knowing Your Computer 'All the Way to the Bottom' (5 min, via)
I initially thought the title was about blobs in firmware, but no, the article is about programming languages, focusing on C.
Interesting, check it out if you're a systems programming nerd.
Give Firefox a chance 🔗
Give Firefox A Chance For A Faster, Calmer And Distraction-Free Internet (10 min, via) is a very good write-up with tips and tricks to maximize the usefulness and also the fun of Firefox.
A must read, and hopefully it may convince some people to switch from Chrome.
Boot sector games 🔗
Boot sector games (10 min, video)
The 8-Bit Guy has fantastic tutorials and reviews of cool old tech. If you want to see what can be done in 512 bytes you definitely need to watch this video.

Use IRC as a private chat 🔗
IRC for DMs (2 min, via) is a quick review of current chat systems and why they suck.
I like crazy, statu-quo breaking ideas, though the practicality of using IRC as a private chat system is nuts. Nuts, as in 90's rad.
Tags: roundup
Links for 2019-11-03
Why 80x25? 🔗
80×25 (5 min, via is fantastic research where author mhoye puts the puzzle pieces together and discovers why our 2019 console emulators launch with a default resolution of 80x25.
I'm not going to spoil it, you will need to read the article. Here's the first paragraph:
Every now and then, my brain clamps on to obscure trivia like this. It takes so much time. "Because the paper beds of banknote presses in 1860 were 14.5 inches by 16.5 inches, a movie industry cartel set a standard for theater projectors based on silent film, and two kilobytes is two kilobytes" is as far back as I have been able to push this, but let's get started.
7000 DOS games in your browser 🔗
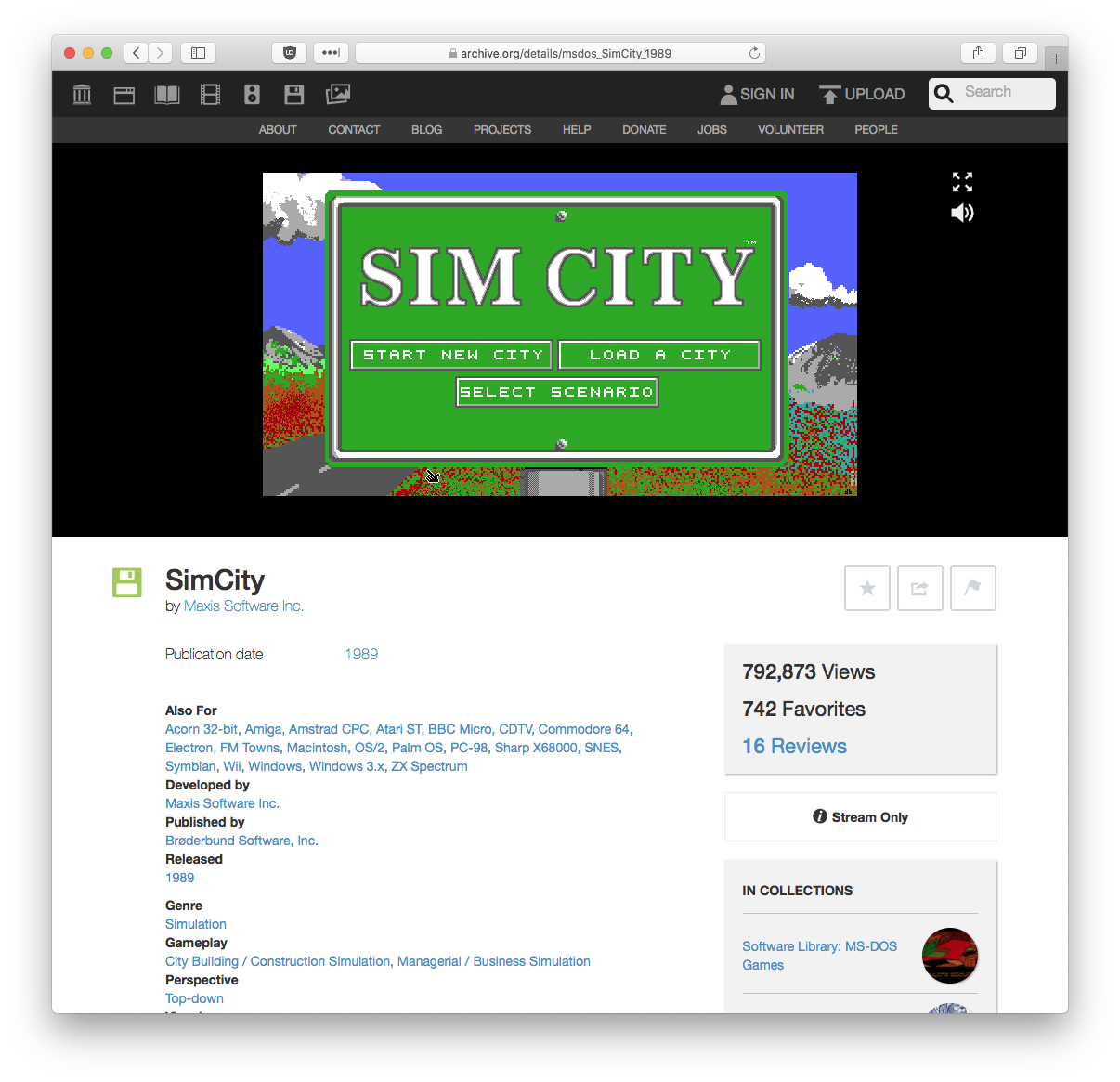
The Software Library: MS-DOS (RH, via) is an outstanding collection of DOS software from the Internet Archive playable in-browser via dosbox-js emulation, including, of course, the aforementioned 7000 games.
Go try it out and waste the rest of this Sunday!
A Gameboy modern clone 🔗
Analogue Pocket, a Gameboy Color/Advance built using modern technology (5 min, via)
An interesting console with hardware for loading original Gameboy cartridges but running with more modern hardware like a hi-res backlit LCD and a rechargeable battery.
I'm always tempted to buy these, but in the end I keep using my NDS Lite as a retro emulator.

NordVPN and TorGuard hacked 🔗
NordVPN confirms it was hacked (2 min, via), NordVPN and TorGuard VPN Breaches: What You Need to Know (5 min, via) and Make yourself an iOS-compatible VPN with OpenBSD
NordVPN told TechCrunch that one of its data centers was accessed in March 2018. "One of the data centers in Finland we are renting our servers from was accessed with no authorization," said NordVPN spokesperson Laura Tyrell.
The attacker gained access to the server — which had been active for about a month — by exploiting an insecure remote management system left by the data center provider; NordVPN said it was unaware that such a system existed.
And
[NordVPN advisory board member Tom Okman] said it was hard to determine if hackers obtained information on the internet usage of Nord users because the company doesn't collect logs of activity on its servers, a selling-point to privacy-conscious customers. 'I think that the worst case scenario is that they could inspect the traffic and see what kind of websites you could visit,' Okman said. He said this would only apply to Nord users who used its Finnish server and were accessing websites that didn't use the secure protocol HTTPS
HN user safeplanet-fesa also raises questions about Tesonet, the parent company of NordVPN
Twitter user @hexdefined details how an attacker could have performed a MITM attempt given what we know about the breach.
Drew DeVault started an interesting thread discussing alternatives on his Mastodon account.
A homemade PCB 🔗
My First PCB! (5 min, via)
Recently I linked to a homemade tutorial on how to make an IC, and this week I found this tutorial where Laura Lindzey explains how to make the jump from a proto-board and make a real PCB at home.
I will always link to these home electronics experiments, I love them.
Spying on children at school 🔗
Gaggle Knows Everything About Teens And Kids In School (2 min, via)
I'm sure that future adults will appreciate having a record of every word they uttered at school /s
Very elaborate, state-targeted Whatsapp attack 🔗
WhatsApp hacked to spy on top government officials at U.S. allies (2 min, via)
A very high-profile attack used a Whatsapp vulnerability "to take over users' phones". Which users? "High-profile government and military officials spread across at least 20 countries on five continents"
Unfortunately, the article doesn't explain how the app exploit propagated upwards to the OS and take full control of the phone, which is the real key of the question.
StarCraft AIs start beating humans 🔗
AlphaStar: Grandmaster level in StarCraft II using multi-agent reinforcement learning (RH, via)
People have been trying to develop Starcraft AIs since forever, but this is the first time that a bot can beat a world champion player.
Our new research differs from prior work in several key regards:
- AlphaStar now has the same kind of constraints that humans play under – including viewing the world through a camera, and stronger limits on the frequency of its actions
- AlphaStar can now play in one-on-one matches as and against Protoss, Terran, and Zerg
- The League training is fully automated, and starts only with agents trained by supervised learning, rather than from previously trained agents from past experiments.
- AlphaStar played on the official game server, Battle.net, using the same maps and conditions as human players. All game replays are available here
Go check the replays now!
The Internet is no longer what it was 🔗
50 years ago, I helped invent the internet. How did it go so wrong? (5 min, via) and I Miss the Old Internet (1 min, via) are a couple nostalgic pieces about the old internet, defending why it was better, because it was more decentralized, more personal, and wasn't just another way to push ads in front of eyeballs.
On a related note, A History of Personal and Professional Websites (10 min) is a series of screenshots showcasing the author's first websites, real nostalgia fuel.
Face recognition to unlock porn 🔗
Australia wants to use face recognition for porn age verification (1 min, via)
What could possibly go wrong?
Chat over the email protocol 🔗
Delta Chat, Instant E-Mail Messaging (1 min, via)
Delta Chat is essentially a GUI over email which displays threads as chat conversations. And I really like that!
This is a really interesting project which, although it will rarely take off on the mainstream, can already argue they already took care of the network effects of their platform. Kind of like the old Google Talk, but universal.
It even includes E2E encryption by default by integrating Autocrypt. The project is actively maintained, so why don't you give it a try?
Running out of IPv4 addresses 🔗
This Time, There Really Are NO IPv4 Internet Addresses Left (1 min, via)
Is it the boy crying wolf again? Is this the digital equivalent of "we will run out of oil in 25 years"?
Some big ISPs still have a large stockpile of IPv4s but others that haven’t deployed IPv6 may have to stretch that out by adopting awkward solutions like internet address sharing (Carrier Grade NAT), which can in some circumstances create problems for internet systems that use unique IP addresses to identify, process and or block user activity.
In other cases we have seen some commercial trading of retired IPv4 address space and this is likely to become more common, at least until the day comes that IPv4 can finally be put to bed.
It seems that we may be in overtime, but there is still a life for IPv4 after all.
At this point I'm not sure what I prefer. Some years ago I even paid my ISP to have a static IP, which I used to host stuff at home. Nowadays, I have a $5/month VPS to host, and I really want to be anonymous at home, so I appreciate address sharing, which hides my real IP to the server, and can only be deanonymized with a judge order to the ISP.
Tags: roundup
Links for 2019-10-20
Bye, Yahoo! Groups 🔗
Yahoo is deleting all content ever posted to Yahoo Groups (1 min, via)
I am torn between "You will not be missed" and "This is like the Geocities shutdown all over again"
In any case, this warrants an F
How to disable Linux Intel mitigations 🔗
HOWTO make Linux run blazing fast (again) on Intel CPUs
(2 min,
via)
is a quick note on the grub parameters required to make Linux faster by disabling the security mitigations
for Intel CPU bugs.
Should you do it? Benchmarks report 10%-15% performance increase with mitigations off. I have personally not taken this trade-off and my mitigations are still on, however, I have not disabled SMT which is the only 100% safe solution.
Personally, on a computer that is constantly running third party code —websites—, I prefer to lose that 15%.
Everything is louder now 🔗
Why Everything Is Getting Louder (15 min, via) blames the tech industry for the rising noise baseline we suffer everyday.
The article focuses on electronics-generated noises, but let me twist it to my agenda.
We must fight against noise pollution.
Unfortunately, in our urban modern lifestyles, we are constantly sharing our space with cars, trains, planes, ambulances, noisy cellphones, TVs, and other sources of unwanted noise.
Some things we can't avoid and, well, we just cope with them.
I hate TVs on bars, dislike ambient music, and loathe people using loud cellphones in public. I carry in-ear headphones and regularly use them even when I'm not listening to any music.
Some people just can't be alone with their thoughts and need constant external stimulus. I understand that, and can even empathize with them. But let the rest of us enjoy our moments of silence.
Both our attention and our peace of mind are precious resources, and anything that wants to deprive us of them, without good reason, is an enemy.
As I read somewhere on the Internet: "Nobody is coming to the beach to listen to their towel neighbour's music."
CO2 levels in offices 🔗
Literally Suffocating In Meetings, A Little (1 min, via) argues that high CO2 levels, which are common in poorly ventilated meeting rooms, have adverse health effects.
The NYT published a piece on CO2 levels and poor decisions, which can be summarized as "high CO2 levels make you groggy and dumb".
I guess the take home message is, watch your CO2 levels as you'd watch temperature, humidity or pollutants.
pg presents new Lisp 🔗
When one of the Lisp wizards releases a new dialect, you listen.
Of course, read the HN comments as they provide more context.
Hardware implants are becoming cheaper 🔗
Planting Tiny Spy Chips in Hardware Can Cost as Little as $200 (5 min, via) is kind of a follow-up to the infamous Bloomberg "The Big Hack" unverified piece.
In this article:
At the CS3sthlm security conference later this month, security researcher Monta Elkins will show how he created a proof-of-concept version of that hardware hack in his basement.
With only a $150 hot-air soldering tool, a $40 microscope, and some $2 chips ordered online, Elkins was able to alter a Cisco firewall in a way that he says most IT admins likely wouldn't notice, yet would give a remote attacker deep control.
Well, now we will start needing verifiable hardware, probably through other trusted hardware testing devices. This is going to be fun.
As a related note, one HN comment points out to Operation GUNMAN - how the Soviets bugged IBM typewriters which contains full details on how the bug works.
An Ode to the File 🔗
Computer Files Are Going Extinct (5 min, via) defends the usefulness of computer files and laments how we are transitioning to different metaphors in the computing world.
Most of the HN comments follow the author's thesis, but I am of a different opinion on this topic.
"Files" are difficult metaphors for most people, and they feel more comfortable when the app hides this structure behind some easier visual object.
This is just another step towards The Great Divide, which will come soon. Computing devices will be split between content creators and content consumers, and consumer devices will be absolutely different in any shape or form to creator devices.
When Steve Jobs' was interviewed at D8 (video, 2:20) where he comes up with the cars/trucks metaphors for PCs and iPads:
"When we were an agrarian nation, all cars were trucks because that's what you needed on the farms." Cars became more popular as cities rose, and things like power steering and automatic transmission became popular.
"PCs are going to be like trucks," Jobs said. "They are still going to be around." However, he said, only "one out of x people will need them."
The move, Jobs said, will make many PC veterans uneasy, "because the PC has taken us a long ways."
You are being tracked 🔗
The Fantasy of Opting Out (10 min, via) is an excellent article by two University professors on how you are being tracked online, not only with cookies and javascript, but also with your devices radios and cross-referencing datasets.
Here's the actionable part:
We can apply obfuscation in our own lives by using practices and technologies that make use of it, including:
The secure browser Tor, which (among other anti-surveillance technologies) muddles our Internet activity with that of other Tor users, concealing our trail in that of many others.
The browser plugins TrackMeNot and AdNauseam, which explore obfuscation techniques by issuing many fake search requests and loading and clicking every ad, respectively.
The browser extension Go Rando, which randomly chooses your emotional "reactions" on Facebook, interfering with their emotional profiling and analysis.
Playful experiments like Adam Harvey’s HyperFace project, finding patterns on textiles that fool facial recognition systems – not by hiding your face, but by creating the illusion of many faces.
The original Macintosh manual 🔗
Thoughts on (and pics of) the original Macintosh User Manual (10 min, via) is a beautiful review of the 1984 Mac manual, complete with high resolution pictures.

I miss printed computer manuals like the Macintoshes and the Commodores.
How to pwn 🔗
Offense At Scale (5 min, PDF) is a good intro to pentesting techniques.
I found that presentation via Defense at Scale where the author suggests strategies to reduce the attack surface.
Both presentations are good, but I liked the former best.
How file formats work 🔗
Designing File Formats (5 min, via) explains how magic numbers and file headers work.
Every programmer should know this. Go read it!
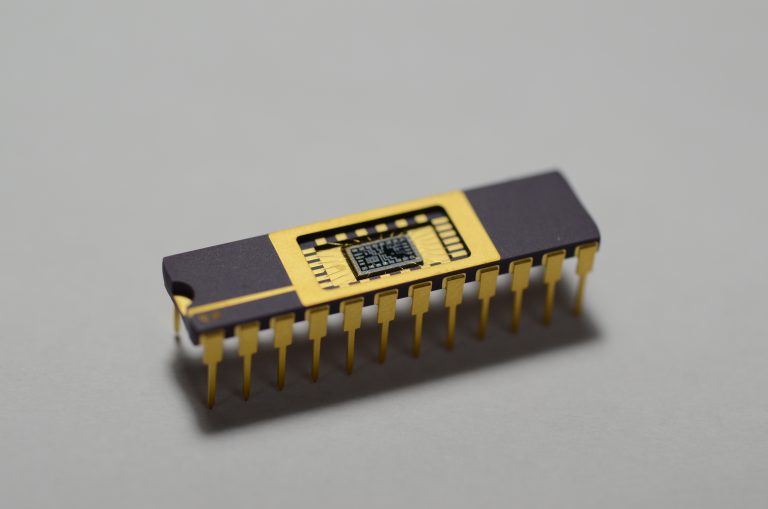
How to make an Integrated Circuit 🔗
On First IC :) (RH, via), Sam Zeloof details how he created his first "homemade" chip on his garage, from design to transistor litography.
He has some advanced machinery available, this is not really a project anybody can do "at home", but it's a very insightful read!
Tags: roundup
Links for 2019-10-13
No common topic this week. Enjoy the links!
New Linux laptops with open source firmware 🔗
System76 Will Begin Shipping 2 Linux Laptops With Coreboot-Based Open Source Firmware (2 min, via)
My endgame is to retire early and create an ecosystem of free hardware + software for a laptop, phone and could environment, like iCloud but totally self-hosted.
Meanwhile, we have to be satisfied with small advances like these laptops running Coreboot.
Kudos to System76, and let's hope the market moves towards this goal.
New graphical toy OS 🔗
SerenityOS: From zero to HTML in a year (2 min), is a visual tour through the development of SerenityOS, a toy OS with graphical capabilities, now able of rendering a webpage using its own web browser.
As a fan of toy OSs, this is awesome.
Ken Thompson's password 🔗
Ken Thompson's Unix password (2 min, via) explains how Nigel Williams hacked Ken Thompson's extremely secure Unix password and it turns out to be a chess move!
From: Nigel Williams Subject: Re: [TUHS] Recovered /etc/passwd files
ken is done:
ZghOT0eRm4U9s:p/q2-q4!
took 4+ days on an AMD Radeon Vega64 running hashcat at about 930MH/s during that time (those familiar know the hash-rate fluctuates and slows down towards the end).
D-Link routers will remain vulnerable 🔗
D-Link Home Routers Open to Remote Takeover Will Remain Unpatched (1 min, via)
I am just going to quote HN user jjguy:
This is the new normal, folks. Consumer technology is manufactured for six to twelve months, but live in our homes for three to five years. Today's manufacturers cannot afford to update software for hardware devices they have already moved on from. Changing that requires a significant upheaval in their business models.
This applies to every "connected device:" printers, cell phones, home routers, refrigerators, thermostats -- you name it.
Your router is your gateway to the Internet. Any flaws on its software will open your home computers and phones to remote attackers.
There is little we can do, except starting to treat our routers like any other computer: make sure it's updated regularly, and when it does not get any security updates anymore, replace it with a newer model.
Twitter misusing 2FA phone numbers 🔗
Twitter admits it used two-factor phone numbers and emails for serving targeted ads (1 min, via)
Only one month ago, Twitter's CEO Jack's account was hacked exploiting his 2FA phone number via "SIM swap" attack.
Now we discover that, like Facebook did, Twitter also used the phone you provided for 2FA to target you with ads.
Shame on Twitter, this is an absolutely shitty practice which will backfire by letting users associate 2FA with a bad thing.
As HN user danShumway explains:
Virtually the entire security industry agrees that using phone numbers for account security is an antipattern because of sim-jacking, and yet swaths of the biggest tech companies in the industry do it anyway.
[...]
In theory, a 2FA over SMS is better than nothing. In practice, it trains customers to be insecure and should be avoided. It trains customers to think that identity verification over text is OK. In practice, you can't trust companies not to use it for advertising, or to start using it as identity verification in the future. In practice, there are very, very few legitimate reasons why a company should ever need my phone number, and pretty much none of them have anything to do with security. 99% of your users should be using a 2FA app instead of a phone number.
Remote exploit on the wild for Android phones 🔗
New 0-Day Flaw Affecting Most Android Phones Being Exploited in the Wild (2 min)
The zero-day is a use-after-free vulnerability in the Android kernel's binder driver that can allow a local privileged attacker or an app to escalate their privileges to gain root access to a vulnerable device and potentially take full remote control of the device.
According to the researcher, since the issue is "accessible from inside the Chrome sandbox," the Android kernel zero-day vulnerability can also be exploited remotely by combining it with a separate Chrome rendering flaw.
Therefore, most Android devices manufactured and sold by a majority of vendors with the unpatched kernel are still vulnerable to this vulnerability even after having the latest Android updates
- Pixel 1
- Pixel 1 XL
- Pixel 2
- Pixel 2 XL
- Huawei P20
- Xiaomi Redmi 5A
- Xiaomi Redmi Note 5
- Xiaomi A1
- Oppo A3
- Moto Z3
- Oreo LG phones
- Samsung S7
- Samsung S8
- Samsung S9
To be noted, Pixel 3, 3 XL, and 3a devices running the latest Android kernels are not vulnerable to the issue.
This is really, really bad. Update as soon as the patches are released, and don't browse untrusted websites meanwhile.
Dockerizing ancient OSs 🔗
Resurrecting Ancient Operating Systems on Debian, Raspberry Pi, and Docker (1 min, via) is a quick note where the author explains how he has dockerized ancient OSs repo to replicate these old environments and play with them in the modern era.
I like this idea a lot and, actually, I have my own folder of virtualised systems with which I play from time to time. I have a perfect replica of my old computers (a DOS + Win31, a Win98 and a WinXP) and run them regularly to feel that good nostalgia.
Your crappy app wastes my brain glucose 🔗
Your app makes me fat (2013, 5 min, via)
This is an extremely interesting article on popular psychology and how willpower is a finite resource which gets depleted.
Willpower and cognitive processing draw from the same pool of resources.
Spend hours at work on a tricky design problem? You're more likely to stop at Burger King on the drive home. Hold back from saying what you really think during one of those long-ass, painful meetings? You'll struggle with the code you write later that day.
Since both willpower/self-control and cognitive tasks drain the same tank, deplete it over here, pay the price over there. One pool. One pool of scarce, precious, easily-depleted resources. If you spend the day exercising self-control (angry customers, clueless co-workers), by the time you get home your cog resource tank is flashing E.
Remember these conclusions: since I read about that link between glucose depletion in the brain and willpower I have been much more aware of my cravings and how to avoid succumbing to them.
The rise of Matebooks 🔗
Void Linux (musl) on the Huawei Matebook X Pro (5 min) is a good review of the Matebook, with some bonus opinions on Void Linux.
I've mentioned many times that I'm unhappy with the current state of Apple hardware, and I have been looking for alternatives.
Old Lenovos are cheap, newer Lenovos are pretty good, and it's nice to know that there's a high quality, affordable laptop in between them.
Remembering the BBSs 🔗
BBSes: Partying Online Like It's 1989 (10 min, via)
The BBS era is one I barely missed, as my early Internet experiences happened around 1996 via IRC, mail and the early web. The article reminisces of this primeval and very popular form of communication that catered to many niches.
On a side note, I just discovered Paleotronic, and it's a great source of retro nostalgia. The topics are interesting, the text is accessible, and it's full of pictures from old magazines. You will probably see it linked a lot here!
A cynical take on HN 🔗
webshit weekly is a weekly commentary on the top HN links.
I really like the author's cynical take, his sense of humor, and the way he interprets comments on the funniest and worst possible way.
You will find gems like:
(Apple Hides Taiwan Flag in Hong Kong)
Whether an old person falls over or a young person stands up, Apple will call the cops.
(Google Cloud is down)
Nobody considers the obvious root cause: Google, being unable to embed ads into TCP packets, has discontinued the product.
(Comparing the Same Project in Rust, Haskell, C++, Python, Scala and OCaml)
Some children play programming language pokemon.
(Facebook reveals its cryptocurrency Libra)
Facebook, unsatisfied with being an unregulated newspaper, post office, and telephone service, decides the only way to recover from years of user-abuse scandals is to become an unregulated bank.
Privacy under attack by US, UK, AU govts 🔗
The Open Letter from the Governments of US, UK, and Australia to Facebook is An All-Out Attack on Encryption (1 min, via)
The EFF explains:
Top law enforcement officials in the United States, United Kingdom, and Australia told Facebook today that they want backdoor access to all encrypted messages sent on all its platforms. In an open letter, these governments called on Mark Zuckerberg to stop Facebook's plan to introduce end-to-end encryption on all of the company's messaging products and instead promise that it will "enable law enforcement to obtain lawful access to content in a readable and usable format."
I don't have much more to add other than linking to my 2015 text on "Think of the terrorists" is the new "Think of the children"
Followup
More problems with Catalina 🔗
In macOS 10.15 Vista (1 min) and Broken (2 min, via), Tyler Hall presents a screenshot of evidence of how low Apple has fallen with its recent UX.
I will definitely not upgrade to Catalina, and there are many others who think like me
I sincerely hope Apple get its act together and starts producing good software and hardware again. These last 5 years have been an absolute hell as an Apple ecosystem user.
Cloudflare is bad, take two 🔗
CloudFlare is ruining the internet (for me) (2016, 2 min, via)
The idea that a single company can negatively influence the experience of such a large portion of the internet for users is kinda scary
I agree with the author. We should stop giving Cloudflare too much power.
This is a company that can cut off internet access for a large amount of users, or seriously hinder it (endless stream of captchas) with the switch of a button.
I would urge everyone to reconsider using CloudFlare as your CDN/DNS/DDOS solution. Being free is not good enough reason to use something, if you are concerned about your site speed there are more important things to look into for optimization before considering a CDN
Most deepfakes are porn 🔗
Most Deepfakes Are Used for Creating Non-Consensual Porn, Not Fake News (2 min, via)
We need to figure out how platforms will moderate users spreading malicious uses of AI, and revenge porn in general. We have to solve the problems around consent, and the connection between our bodily selves and our online selves. We need to face the fact that debunking a video as fake, even if it's proven by DARPA, won't change someone's mind if they're seeing what they already believe. If you want to see a video of Obama saying racist things into a camera, that's what you'll see—regardless of whether he blinks.
The Department of Defense can't save us. Technology won't save us. Being more critically-thinking humans might save us, but that's a system that's lot harder to debug than an AI algorithm.
Last month I linked to a Facebook initiative to detect deepfakes and it seems that the deepfake problem is starting to get mainstream.
Good.
Tags: roundup
Links for 2019-10-06: Retro Nostalgia
The topic for this week is nostalgia. As usual, the on-topic links appear first, then the classic medley, and finally some follow-up.
Retro Nostalgia
DOS compatible Macintosh from 1995 🔗
Apple's MS-DOS Compatible 486 Macintosh from 1995! (10 min, via)
Famous retro youtuber LGR does a short tour of this retro Macintosh that contains a card with a 486 and can run DOS.
Demo with sound in 64 bytes 🔗
into war 64b (1 min, via) is a 3D animation, or demo, with sound, in only 64 bytes of DOS assembler.
This Reddit thread does a code analysis, and reveals the many tricks the demo uses.
Are RTSs dead? 🔗
What Happened to the Real Time Strategy Genre (2 min, via) is a good analysis of why there are no good RTS games.
Having played Starcraft 2, I must admit that I liked Starcraft better. Even War3, as enjoyable as it is, lacked playability in comparison with the original Starcraft.
Nowadays I don't play many games, so I don't mind installing SC from time to time and playing some campaigns. Who needs modern RTSs when we already reached perfection in 1998? ;-)
Four column ASCII 🔗
Four Column ASCII (2017, 5 min) explains why Ctrl-H is backspace, Ctrl-[ is Escape, and other control codes.
Curious and enlightening. Every UNIX user should learn this, and it's not really common knowledge.
SNES enhancement chips 🔗
SNES enhancement chips (2 min, via) is a tweetstorm detailing different chips that SNES cartridges used to provide extra features to the base console.
In the HN discussion, user jordigh links to a great series of posts detailing how the Super Game Boy works, which is maybe even more interesting and in depth than the original tweetstorm!
How X11 works 🔗
Explanations (RH, needs JS, via) is a series of amazingly well-done and well-explained, in-website demos on how X11 works.
Yes, the demos embed an X11 server inside your browser and allow you to understand how the protocol works!
If you're even vaguely interested in how your computer is rendering the content you're reading right now, check out this link.
Links of the week
Dev backlash to macOS 10.15 🔗
Sorry macOS users, but Apple has gone too far for some of us devs (1 min, via, HN discussion), and Thoughts on Cocoa (1 min, via) are just two of the increasing number of articles against 10.15 breaking backwards compatibility.
Catalina is going to drop 32-bit support and many old, unmaintained applications are going to stop working.
I personally use a few of them, and it's making me strongly consider not upgrading to 10.15.
The computer on the Voyager 🔗
"Uptime 15,364 days - The Computers of Voyager" by Aaron Cummings (40 min, via)
The Voyager 1 and Voyager 2 space probes, both launched in 1977, each had a primary objective to explore Jupiter and Saturn. This goal was achieved by 1981. Yet Voyager, NASA's longest running mission, has continued to this day. Both Voyager probes are still operating, and returning scientific data from outside our solar system.
This talk explores the computing systems of Voyager - the systems which enable remote control of the spacecraft, and provide for the recording and return of data to Earth. These systems have proved to be both adaptable, durable, and resilient in support of a scientific undertaking now in it's fifth decade.
What can we learn from the engineering of Voyager's computing systems? Why have they survived for so long in the harsh environment of space? What is involved in patching a system from a billion miles away? And what does the future hold?
I love these feats of engineering.
Windows 10 pushes you to create a Microsoft account 🔗
MS has removed the "use offline account" option when installing (1 min, via)
It seems that the title is misleading. Reddit user Froggypwns explains (emphasis mine)
They have not removed it, it just is not visible by default if you are connected to the internet. Either run the setup without being connected to the internet, or type in a fake phone number a few times and it will give you the prompt to create a local account.
Other Reddit users provide workarounds around this, but the main point is that the Windows user experience is worse than ever.
The real work that executives do 🔗
What do executives do, anyway? (10 min, via) is an excellent, let me say it again, excellent read on how executives should behave in order to get the best possible outcomes.
Let me give you a sneak peek:
What executives need to do is come up with organizational values that indirectly result in the strategy they want.
[...]
Why will employees embrace whatever weird organizational values you set? Because in every decision meeting, you enforce your values. And you fire the people who don't line up. Recursively, that means executives lower down the tree will do the same, because that itself is one of the values you enforce.
Really, if you are in an executive position, go ahead and read it.
Followup
Wrap-up on TVs tracking you 🔗
Three recent papers uncover the extent of tracking on TVs (Tweetstorm, 5 min, via) mentions the two studies linked here previously, Tracking you with TV ads and IoT products expose personal information, and links to another one in the same line.
If you are interested in learning more, Arvind Narayanan's tweetstorm is thorough and to the point, explaining the main conclusions of each paper. His conclusions:
There are steps we can take. Stay away from vendors whose business model is targeted ads. Every device is a potential tracker; do your research before buying. Install tools that give you control, such as Pi-hole, even if imperfect. Install a monitoring tool on your home network.
and
These individual steps are not enough: we need collective action. Researchers must keep doing our part; we look forward to teaming up with journalists, civil society organizations, and the public, so that we can choose our future, not sleepwalk into it one channel at a time.
As usual, the HN discussion provides interesting viewpoints too.
Tags: roundup
Links for 2019-09-29: We live in a cyberpunk future
This week has a lot of "holy crap we live in the future" news so I decided to start this new format where every roundup has a main topic.
After them we will jump to our usual medley of programming + geeky stuff.
In the end you will find some follow-up of past topics.
Hope that you like it!
Cyberpunk 2019
Boston Dynamics 🔗
Latest from Boston Dynamics (1 min)
What a perfect video to start this compilation with.
Just watch it:
Now, close your jaw, and choose one reaction:
- Amazing!
- Terrifying!
(Yes, it's both)
Facial recognition in the EU 🔗
No es China, es Madrid: el pago facial llega en fase de pruebas a los autobuses de la EMT
(Spanish link: "This is not China, it's Madrid: facial payment tests launch on metropolitan buses", 1 min)
After the initial shock, we should actually ask ourselves whether facial payments are more or less private than paying with a personal card. After all, you're being tracked nonetheless.
In any case, this is the future we're moving towards: more convenient, less anonymous.
Government backdoors on chat apps 🔗
Facebook, WhatsApp Will Have to Share Messages With U.K. Police (1 min, via)
As usual, the title is heavily editorialized and I recommend reading the HN discussion to understand the actual situation.
Regardless of the news, it is worrying that governments want to force chat apps to share user conversations with the police. The real question is, will they ban encryption at some point? Will this decision be clear to the user, i.e. will we know that our conversations are no longer secure, and therefore be more restrained in what we share? Or will they lie to us and just install backdoors that silently spy on our texts without our knowledge?
This is a truly worrying trend.
AI playing hide and seek 🔗
Emergent Tool Use from Multi-Agent Interaction (5 min, via) presents a paper and a video of a multi-agent AI system evolving strategies to play hide and seek with a few spatial tools like ramps, barriers and boxes.
Check out the video, it's quite interesting, especially the fact that hiders collaborate amongst them to build forts, and seekers find unexpected uses for their tools, like jumping on top of boxes.
Multi-agent goal-seeking is not new, but it is a great way to discover algorithms and strategies that we had not previously thought of.
Links of the week
Functional programming in Python 🔗
Learn Functional Python in 10 Minutes
(10 min,
via)
is a good overview of lambdas, map, reduce, filter and others.
Every good Python programmer should know these.
Review of chat systems 🔗
Thoughts on improving chat systems (5 min to RH, via) reviews open chat systems (IRC, XMPP, Matrix) and compares them to other established protocols and apps.
Unfortunately, the dream of having A Unified Chat System was only true for a couple years when both Google and Facebook supported XMPP, but then it went away.
Chats are siloed now, and it doesn't look like this is going to change soon :(
Look at the night sky 🔗
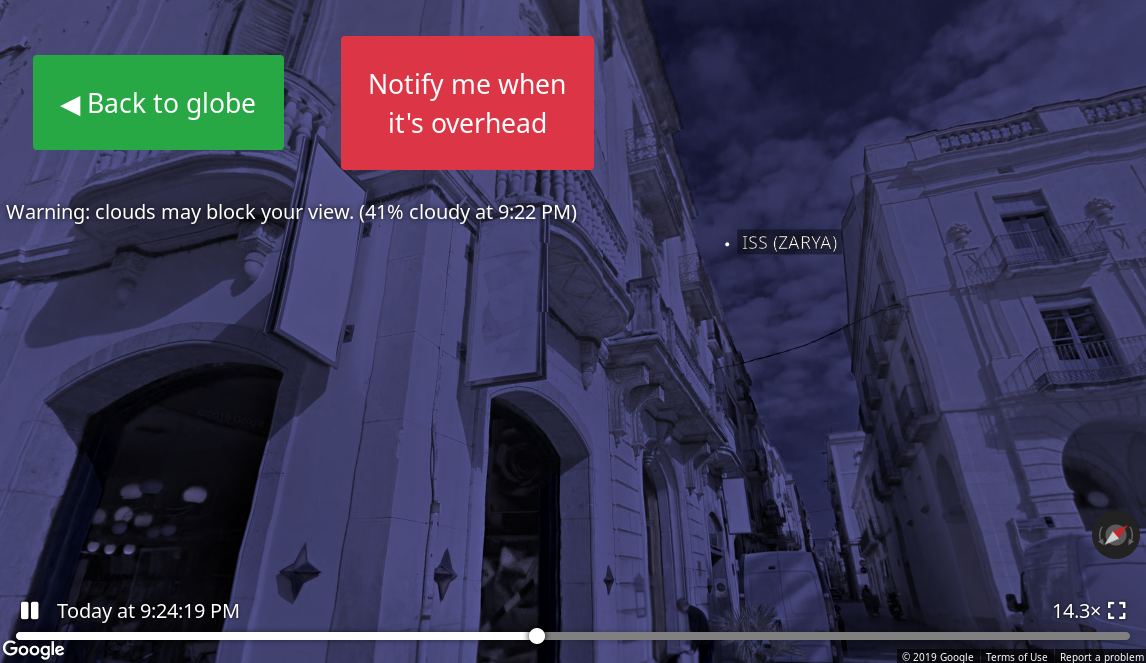
See a Satellite Tonight. No Telescope Required (5 min, needs JS, via) is a webapp that helps you spot satellites and the ISS traveling through your location.
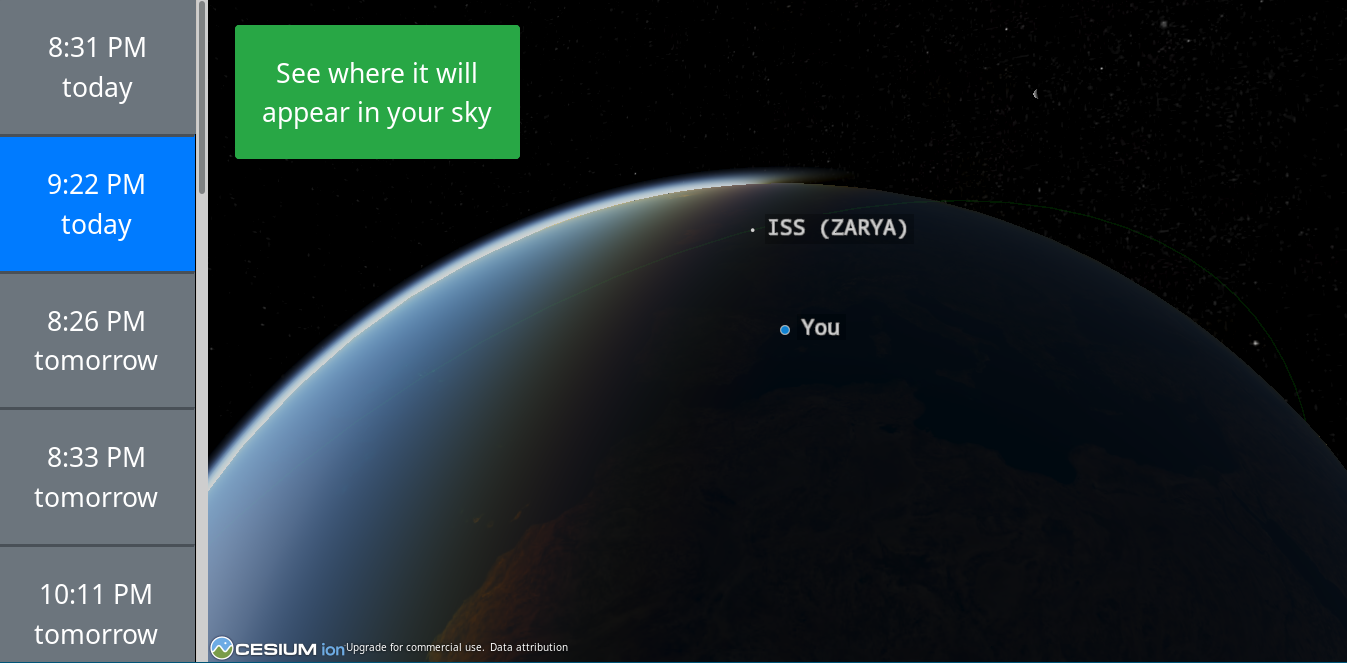
I saw the ISS last Friday, since it was passing near Barcelona on a 73° angle, almost optimal to watch.
It was amazingly minimalistic. You see a small white dot darting through the sky; you know it is just a very fast plane, but looks like a star.
After three minutes it was gone. There they go, there are people in that small dot, orbiting the Earth. It is an incredible feeling.
Go ahead, look at the night sky today, and admire both the stars, the planets, and human-made orbital bodies.
This webapp even gives you a street view of the satellites so you know exactly where to look at in the sky. Amazing!
Followup
Quitting social media 🔗
On I Quit Social Media for a Year and Nothing Magical Happened (5 min, via) and its follow-up Having a Social Life Without Social Media (2 min), Josh C. Simmons explains what happened after he decided to quit Facebook and Instagram.
I agree with the author's premises: quit social media and you will be happier and have more time to work on productive tasks.
The detailed mental phases he went through are interesting, though. He realized that he was taking most pictures with the intent of sharing them and, now that he had no social network to share them on, he just stopped taking them. Another one is that when you no longer get "life updates" through social media, you have more things to talk about when you face-meet your friends.
A good read overall, not your typical "FB sucks I am quitting" argument you see plastered over Reddit.
If you want to read more on the topic, I have written about social media extensively in the past: how I missed Facebook after quitting it, why it was a good move (for the company) to buy WhatsApp and Instagram, and why the "Like" culture is just a reflection of human nature
More on Firefox and DoH 🔗
Turn off DoH, Firefox. Now. (5 min, via) and especially Centralised DoH is bad for privacy, in 2019 and beyond (5 min, via) explain why the Firefox-Cloudflare integration is a bad idea much better than I did and also provide information on how to disable it.
After reading arguments on both sides, I stand by my initial reaction: this is a bad idea because it centralizes DNS, which ought to be a decentralized service.
To add insult to the injury, it sends that traffic to a country with no privacy laws and a provider who leaked HTTPS data in the past.
Sorry, Mozilla, but the cons overwhelm the pros.
Tracking you with TV ads 🔗
Is your smartphone listening to everything you say? We asked the experts (2017, 5 min, via) alerts (emphasis mine):
Last year the CDT alerted the Federal Trade Commission (FTC) to a technology called SilverPush. It uses audio beacons to track your activities across devices:
Your TV emits a tone during a commercial break, a tone that’s inaudible to you, but your phone is listening for it. Now they can link the TV and phone as belonging to the same person.
Make sure you can trust your phone—and your friend's.
Remember that you are always talking near a microphone connected to the internet.
Tags: roundup
Link roundup for 2019-09-22
Welcome to this roundup! Starting with this issue, all headers will contain a permalink 🔗 to reference them inside the document.
Amazing pics taken with a cellphone 🔗
iPhone 11 Pro Camera Review: China (5 min) is a review of the iPhone camera through the eyes of a professional photographer.
If somebody told you five years ago that those pictures were taken with a cell phone, you wouldn't have believed them.
The interesting thing is that, in hindsight, it was inevitable. As an amateur, I used to take many pics with different exposures with my crappy reflex and then post-process them at home. Color adjustments, crops, panoramas, HDR...
I remember trying lots of software to extract the most of my raw files, and managing to get great shots by combining the definition of low ISOs with the light of higher ISOs. I have nice pics of dark chapels and cozy restaurants. It was only a matter of time that cellphones started doing that process automatically on the same phone.
For all the criticism cellphones receive by a sector of the population, having a fantastic camera in your pocket at all times is a net win for mankind. I'm truly happy that computational photography has finally happened and that it's available for everyone.
The bash bible 🔗
pure bash bible: A collection of pure bash alternatives to external processes
(RH,
via)
is a cookbook with a lot of bash recipes.
As a bash fan myself, this content is 100% gold.
When watching TV, you are the product 🔗
Information Exposure From Consumer IoT Devices: A Multidimensional, Network-Informed Measurement Approach (10 min, via)
Through a total of 34,586 [...] experiments, we characterize information exposure [...] and whether there are unexpected exposures of private and/or sensitive information (e.g., video surreptitiously transmitted by a recording device).
FT published a paywalled article with a more accessible text. You can bypass the paywall by searching the title on Google and clicking on the result.
The only conclusion is: Minimize the number of Internet-enabled devices.
More specifically, don't use Smart TVs, or internet-enabled hardware from companies that either (a) don't know how to do secure software, or (b) have a strong incentive on selling your data.
Critical software in hands of volunteers 🔗
The Internet Relies on People Working for Free (5 min, via) is a good reminder that the software that keeps everything running is maintained by volunteers.
Not much to add, just a big thank you to all of them. And, if your business relies on volunteer-developed software, you should have a Plan B in case something happens.
Stallman resigns from the FSF and MIT 🔗
Resignation (1 min, via) and Richard M. Stallman resigns (1 min, via) succintly explain how rms has resigned from his bigger political responsibilities.
Stallman was on fire after a Vice article criticising his mails where he kinda provides excuses/justifications about people accused of having sex with coerced minors.
The Epstein-Minsky-pedophilia topic is so sensitive that Stallman, despite being in the spectrum, should have known better than to talk about it on MIT mailing lists.
Yes, his latest mails and opinions have been misrepresented. Yes, as a very public figure, he should have been more careful and do not enter a discussion over semantics, as he always does, on such a sensitive topic as pedophilia. Yes, it seems that the white old guy argument has precedence over the ableism argument, since anybody who has interacted with him in the slightest knows he is barely functional. Yes, him defending "consensual" sex with minors in the past as something acceptable did not help at all, and neither did the fact that he's a jerk to most of the people he interacts with—speaking from own experience, unfortunately.
The saddest part is, despite his social limitations, and holding a horrible stance for many years, he was making an honest effort to change for the better.
But that doesn't matter. Child sex is a storm that engulfs anybody that comes near it. The crime is so vile that it is probably warranted.
Still, I find it unjust that this was, as many people said, "the straw that broke the camel's back". Stallman was not defending pedophilia this time —sigh—, and there should not be any argument that people cannot discuss. However, that was neither the place nor the moment.
As reddit user im_not_juicing intelligently states,
I think we all could learn a lesson here: it is not worth to waste our lifes arguing over the Internet about random stuff.

If you want to read more, check out the HN discussion, this thread on /r/stallmanwasright and pg's essay "What you can't say"
Update 2019-09-22 22:08. Thomas Bushnell has a very informed and reasonable opinion on this topic that you definitely should read.
6502 homebrew projects 🔗
Build a 6502 computer (RH, via) is a tutorial on how to build a basic board with a 6502 and program it.
I'm a huge fan of development boards myself, and have half a dozen at home. But I had never seen one with a 6502.
Watch his "Hello, world" from scratch on a 6502 video, too.
On a related note, David Murray, the 8-bit guy is also designing a 6502-based computer
Set up your own mailserver 🔗
Setting up a mail server with OpenSMTPD, Dovecot and Rspamd (30 min, via)
is yet another tutorial that tries to get engineers to host their own mail.
I do it myself, and though setup is easy, deliverability is a real pain. Your emails go directly to spam, or nowhere at all, and there is no real way to debug it.
Tags: roundup
Link roundup for 2019-09-15
Twitter CEO gets his Twitter account hacked
Hackers Hit Twitter C.E.O. Jack Dorsey in a 'SIM Swap.' You're at Risk, Too. (5 min, via)
Here's how it works:
Sometimes hackers get phone numbers by calling a customer help line for a phone carrier and pretending to be the intended victim. In other recent incidents, hacking crews have paid off phone company employees to do the switches for them, often for as little as $100 for each phone number.
Once the hackers have control of the phone number, they ask companies like Twitter and Google to send a temporary login code, via text message, to the victim’s phone. Most major online services are willing to send those messages to help users who have lost their passwords.
But the temporary code is sent to the hackers.
2FA over SMS is not the best, but not the worst. The problem is that Twitter's implementation was bad, as it allowed you to reset anybody's password with —this is key— only their phone number.
HN user zaroth explains it well:
Twitter uses SMS as a single factor, because you can reset the password with only access to the text message. If Twitter was using SMS only as a 2nd factor, this attack would not have worked without also knowing Jack’s password or having access to his email. Twitter’s password reset function could require an SMS code and then send a password reset email to complete the process.
While user fulafel summarizes it in a tweet-like sentence:
It's really ½FA, worse than 1FA authentication because it's sufficient to clear any 1 of the 2 factors.
Favorite old books?
Ask HN: What are your favorite books or essays written at least 100 years ago? (10 min - RH) user marceee0901 asks an interesting question, and the replies are very interesting, too.
Some non-tech books surface to the top, like:
- The Count of Monte Cristo
- Meditations
- The Prince
- Anna Karenina
And user cbailes suggests a site I wasn't aware of: The Hacker Classics, a list of HN links with a date on the title, e.g. (1928), sorted by this date.
Facebook fighting deepfakes
In Creating a data set and a challenge for deepfakes (2 min, via), Facebook announces that they are committing $10M to create a dataset of True Positive deepfakes so researchers can develop tools to detect them.
Thanks, Facebook.
Firefox sending DNS queries to Cloudflare
What's next in making Encrypted DNS-over-HTTPS the Default (2 min, via) Mozilla explains why they will send all your DNS queries to Cloudflare.
I do not like this on the slightest bit. The current DNS system is good as it is now; you can choose to trust
your ISP, typically the default choice, or use a third party system like Google's 8.8.8.8
However, the browser should definitely NOT run their own DNS subsystem and bypass the OS or network default.
Neither should us collectively, as a matter of principle, give too much power over the internet infrastructure to a single company. We already made this mistake with Google (search and mail) and Facebook (personal data) and, well, I rest my case.
And, though not related to my point, let's not forget that Cloudflare apocalyptically screwed up in 2017 by unknowingly leaking HTTPS traffic in plain text
Overall, a bad idea, Mozilla, and you should step back on this.
The Senior Engineer's Checklist
A Senior Engineer's CheckList (5 min, via) is a good compilation of both technical and human tasks that a senior engineer should be aware of.
Really good read, check the author's comments at the via link.
Sunsetting Python 2
Sunsetting Python 2 (2 min) explains why Python 2 needs to die. And it does so in an excellent and thoughtful way, providing real answers to real questions that Python 2 users may have, both experts and novices.
I especially like the last two FAQ points:
I didn't hear anything about this till just now. Where did you announce it?
and
How can I make sure announcements like this don't surprise me again?
Finally, I found it brilliant how they emphasize that this decision will benefit the whole community by optimizing volunteers' time. The word volunteer appears all over the FAQ, which I think is a great way to avoid pointless discussions: volunteers don't owe you anything, please use Python 3 now.
A civ1 clone in Excel
I'm creating a Civ1 clone - in Excel (RH, via)
Super impressive and really cool!
A full featured toy OS that runs Doom
Soso, a simple unix-like operating system (1 min, via) is a nice toy OS with a lot of features:
Soso is a 32-bit x86 operating system and its features are
- Multitasking with processes and threads
- Memory Paging with 4MB pages
- Kernelspace (runs in ring0) and userspace (runs in ring3) are separated
- Virtual File System
- FAT32 filesystem using FatFs
- System calls
- Libc (Newlib is ported with only basic calls like open, read,..)
- Userspace programs as ELF files
- mmap support
- Framebuffer graphics (userspace can access with mmap)
- Shared memory
Soso has Libc, so existing applications depending only on a small part of Libc can easly be ported to Soso. I have managed to build and run Lua and Doom on Soso!
You can download an ISO and run it with qemu, go ahead and try it!
Tags: roundup
Link roundup for 2019-09-08
Welcome to this week's roundup. From now on I'll be including an estimated read time for each link, so you have a general idea of what to expect.
You will start seeing the term Rabbit Hole, or RH for short, to indicate those links that can lead to hours and hours of new and interesting discoveries.
More on the iOS implant
In A message about iOS security (2 min, via), Apple responds to the terrifying implant that was reported last week.
First, the sophisticated attack was narrowly focused, not a broad-based exploit of iPhones "en masse" as described. The attack affected fewer than a dozen websites that focus on content related to the Uighur community.
[...]
Google's post, issued six months after iOS patches were released [...] We fixed the vulnerabilities in question in February — working extremely quickly to resolve the issue just 10 days after we learned about it
A bit of damage control and down-toning Google's report, however, I still stand by my take on it.
Apple Music official web app
Apple Music launches on the web (via)
Finally.
Apple is serious about competing with Spotify, which is good. However, I couldn't make it work on Linux (Chrome and Firefox). Let's see if they support these configurations soon.
Librem 5 phone shipping
Librem 5 Shipping Announcement (1 min, via)
The Librem 5 is here. I'm very curious as to how the phone is going to turn out and surely will have an eye opened for the first reviews.
Google keeps selling their user data
Brave uncovers Google's GDPR workaround (10 min, via)
Google claims to prevent the many companies that use its real-time bidding ad (RTB) system, who receive
sensitive data about website visitors, from combining their profiles about those visitors. It also announced that it had stopped sharing pseudonymous identifiers that could help these companies more easily identify an individual, apparently in response to the advent of the GDPR.But in fact, Brave's new evidence reveals that Google allowed not only one additional party, but many, to match with Google identifiers. The evidence further reveals that Google allowed multiple parties to match their identifiers for the data subject with each other.
Don't use Google.
How does BitTorrent work?
How Does BitTorrent Work? a Plain English Guide (15 min) is a long and comprehensive explanation of the BitTorrent protocol, written in a language that most engineers will understand. There are many emojis and beautiful illustrations, but this is definitely not something you can send your mom.
How Netflix uses Python
Python at Netflix (5 min, via) details a series of Python tools and how they are used at Netflix.
Some may be interesting for you, some may be not. Skim the text and focus on whatever catches your eye!
How Tetris decides which piece comes next
The history of Tetris randomizers (1 min, via) is a short and interesting read on how Tetris chooses the next piece, with pros and cons of each approach which affect released games, like the NES version.
If you want to enter the Tetris Nirvana, check out Tetris.wiki (RH, via)
A historical tour of software and websites
The Version Museum (RH) "showcases the visual history of popular websites, operating systems, applications, and games that have shaped our lives."
If you like this website, you can't miss the GUIdebook Gallery and the GUI Gallery, both of them are excellent, and especially the latter contains literal screen shots of very old, obscure systems.
More on deepfakes
The Verge reports that Another convincing deepfake app goes viral prompting immediate privacy backlash (1 min), and TheNextWeb informs that Fraudsters deepfake CEO’s voice to trick manager into transferring $243,000 (1 min)
We all knew this day would arrive, and now it's here—it's been here for a couple years now, really.

In the 90s, Photoshop became a verb that stands for changing a picture in such a way that the end result is fake but believable. Technology now allows us to do the same with video and audio.
This is a very interesting social challenge. Not being able to trust any picture/video/audio will for sure change concepts like proof and deniability which are core for law and society.
Cool CSV utils for the command line
eBay has a Github repo (1 min read, more to try the code, via) with sort of a "framework" to handle csv/tsv files from the command line.
User JimmyRuska also contributed with more tools and other users have linked to their favorite scripts in the comments. I highly recommend you check out the discussion if you work with csv files regularly. Being able to transform data quickly on the terminal is a true superpower.
Of course, you can convert any csv file into a SQL database using sqlite's .mode csv, which
I recommend even more for huge datasets that don't fit in memory.
Read time: 1 minute to check it out, more if you actually run the code
Learning how to read
User vilvadot asks HN how do others read a book (5 min to RH)
The answers are very interesting, and user guidoism recommends How to Read a Book: The Classic Guide to Intelligent Reading (Wikipedia link), and user Scarbutt links to a University of Michigan's 11-page document How to Read a Book, v5.0
Check it out if you want to improve your reading techniques
Tags: roundup
Link roundup for 2019-09-01
Facebook keeps spying on its users
Jane Manchun Wong, a security researcher, writes:
Facebook scans system libraries from their Android app user’s phone in the background and uploads them to their server
This is called "Global Library Collector" at Facebook, known as "GLC" in app’s code
It periodically uploads metadata of system libraries to the server
Don't use Facebook.
New modern book on Lisp
Loving Common Lisp, or the Savvy Programmer's Secret Weapon, free to read here (via) is a very accessible and modern take on Common Lisp by veteran author Mark Watson.
It covers the basics, but also not-so-common topics like network programming, NoSQL databases, NLP and NNs. Definitely worth a look if you want a good Lisp book, and definitely worth it to support the author by purchasing a copy.
On browser privacy
- What happens when you launch Google Chrome for the first time on a Windows 10 machine?,
- What happens when you launch a fresh install of Firefox?,
- What happens when you install the Edge (Chromium) Beta build and run it for the first time?, and
- What happens with other minor browsers
(via) are a series of posts by Jonathan Sampson analyzing how browsers phone home on first launch and its privacy implications
My personal opinion is that Mozilla shoud try to do better. However, since Google is one of the big donors of the Mozilla Foundation, their hands probably will always be tied.
Windows' and Linux's birthday
What would you like to see most in minix?, asked Linus the 25th of August, 1991, in comp.os.minix. (via)
Coincidentally, Windows 95 was released August 24th, 1995 with such a big marketing campaign that I still remember even though I was a kid.
And, in case you haven't seen it: "The Most 90s Video Ever," Microsoft Windows 95 Video Guide - Jennifer Aniston & Matthew Perry
More bash black magic trickery
Seven God-Like Bash History Shortcuts You Will Actually Use
(via)
goes deep into the !! argument expander.
Definitely give it a read, and if you're interested in more bash tricks, let me plug in my own compilation of commandline tricks
Youtube nostalgia
Youtube Decade (via) is a nice daily nostalgia dose.
10 years of Internet Time is like 100 years IRL.
Tags: roundup
Link roundup for 2019-08-25
I tried to start a link roundup last year. Let's see if this time I can post more than once a year.
Tiny terminal multiplexer
mtm (via) is the Micro Terminal Multiplexer, which is written in about 1000 lines of code.
I have been a screen fan for a long time
and recently tried tmux, which I ditched because I just can't get around its windowing metaphors
and scrollback behavior. I will try mtm for sure.
Nostalgia trip to the 90s
Poolside FM is a website that simulates a Classic Mac desktop environment playing 90s music and video clips.
Definitely give it a try!
On plaintext email
Use plaintext email (via) and its open reply, stop gatekeeping email are part of an eternal discussion on whether email should be pure plaintext or not.
I'm personally a big proponent of plaintext email and even launched a startup around it, but I can also see the benefits of rich text email.
In the end, email is a tool, and as such it should be used as conscientiously as one can.
Recaptcha is evil
There is no evil like reCAPTCHA (v3) argues that Google is weaponizing reCAPTCHA.
My feeling is that reCAPTCHA is now more of a bother to the "good guys" than the "bad boys" and, as such, we need a replacement for it.
I personally use a heavily secured browser to browse the internet (blocking js, ads, and more) and, therefore, I encounter a lot of reCAPTCHAs daily. Sometimes they are so difficult to solve that I even wonder if I am the robot.
Warshipping Wi-Fi devices
With warshipping, hackers ship their exploits directly to their target's mail room (via) is an astounding tale of how clever techniques can bring a virus into your literal doorstep.
The researchers developed a proof-of-concept device — the warship, which has a similar size to a small phone — into a package and dropped it off in the mail. The device, which cost about $100 to build, was equipped with a 3G-enabled modem, allowing it to be remote-controlled so long as it had cell service. With its onboard wireless chip, the device would periodically scan for nearby networks — like most laptops do when they're switched on — to track the location of the device in its parcel.
"Once we see that a warship has arrived at the target destination's front door, mailroom or loading dock, we are able to remotely control the system and run tools to either passively, or actively, attack the target's wireless access," wrote Henderson.
Software should be fast
Fast Software, the Best Software (via) provides important argumes as to why software should be fast, and not just because
A typewriter is an excellent tool because, even though it’s slow in a relative sense, every aspect of the machine itself operates as quickly as the user can move. It is focused. There are no delays when making a new line or slamming a key into the paper. Yes, you have to put a new sheet of paper into the machine at the end of a page, but that action becomes part of the flow of using the machine, and the accumulation of paper a visual indication of work completed. It is not wasted work. There are no fundamental mechanical delays in using the machine. The best software inches ever closer to the physical directness of something like a typewriter.
Well-formated, royalty-free ebooks
Standard ebooks (via) is a compilation of royalty-free ebooks with proper formatting.
There's not much to add. Great job!
AMD is making a comeback
AMD lands Google, Twitter as customers with newest server chip (via) is just another step in the Intel chip debacle.
Hobbyists and armchair experts have been expecting this for a long time, but for an important company like Google or Twitter to make the switch means the tide is truly turning.
I don't hold any animosity towards Intel, besides being unhappy with the crap thay have been doing with their chips (bugs and ME). In any case, competition is good, and the x86 server market was in much need of it.
Bicycle for the mind
Bicycle for the mind (via) explores the not so famous Steve Jobs' quote that "a computer is a bicycle for the mind".
This article is excellent, providing not only the original video, but also looking for the original research text that Jobs was referring to in the interview, and complementing it with other videos and marketing materials.
As a Jobs fan, I spent more time on that page that I'm willing to admit. But we have to admit that "bicycle for the mind" is one of the greatest metaphors of our time.
Why are switches clicky?
Switches are Clicky; Here's Why (via) is an extremely cool video about how electricity works, and why we have switches at home.
Again, electricity is one of the topics that fascinates me the most. Read below...
The Electricity FAQ
ELECTRICITY FAQ is a very long document that you should read if you'd like to understand how electricity works. Heck, I'll even say that you should read it even if you think how electricity works.
Tags: roundup
Roundup: Welcome, on news, bad tools and great tools
I'm starting a series of posts with a summary of the most interesting links I found. The concept of "social bookmarks" has always been interesting, but no implementation is perfect. del.icio.us was probably the closest to a good enough service, but in the end, we all just post them to Twitter and Facebook for shares and likes.
Unfortunately, Twitter search sucks, and browser bookmarks rot quickly. That's why I'm trying this new model of social + local, not only for my readers but also for myself. Furthermore, writing a tapas-sized post is much faster than a well-thought one.
Hopefully, forcing myself to post periodically —no promises, though— will encourage me to write regular articles sometimes.
Anyway, these posts will try to organize links I post on my Twitter account and provide a bit more of context.
While other friends publish newsletters, I still believe RSS can work well, so subscribe to the RSS if you want to get these updates. Another option is to use some of the services which deliver feeds by email, like Feenbox which, by the way may never leave alpha, so drop me an email if you want an invitation.
Nostalgia
RTVE, the Spanish public TV, has uploaded a few Bit a bit episodes. It was a rad early-90s show that presented video games and the early Internet.
On news
I quit reading news 3 years ago. A recent article from Tobias Rose-Stockwell digs deep into how your fear and outrage are being sold for profit by the Media.
@xurxof recommended a 2012 article from Rolf Dobelli, Avoid News. Towards a Healthy News Diet
LTE > Fiber
A veces estoy en casa y desactivo el wifi del móvil para navegar con 4G porque me falla el router o el internet. Quién nos lo iba a decir.
— Carlos Fenollosa (@cfenollosa) July 23, 2017
I was having router issues and realized how my cellphone internet is sometimes more reliable than my home fiber.
It seems to be more common than you'd think, read the Twitter replies! XKCD also recently posted a comic on this
Journaling
There was a discussion on Lobste.rs on tools to journal your workday, which was one of the reasons that led me to try out these roundup posts.
New keyboard
I bought a Matias Clicky mechanical keyboard which sounds like a minigun. For all those interested in mechanical keyboards, you must watch Thomas's Youtube channel
The new board doesn't have a nav cluster, so I configured Ctrl-HJKL to be the arrow keys. It gets a few days to get used to, but since then, I've been using that combination even when I'm using a keyboard with arrow keys.
Slack eats CPU cycles
Uso de CPU: Pycharm creando imagen de Docker. Dropbox sincronizando 3000 archivos. Slack haciendo absolutamente nada con la ventana cerrada. pic.twitter.com/D0UZK4oGv5
— Carlos Fenollosa (@cfenollosa) July 26, 2017
Slack was eating a fair amount of my CPU while my laptop was trying to build a Docker image and sync 3000 files on Dropbox. Matthew O'Riordan also wrote Where’s all my CPU and memory gone? The answer: Slack
Focus, focus, focus!
I'm a brain.fm subscriber and use it regularly, especially when I'm working on the train or in a busy cafe.
musicForProgramming() is a free resource with a variety of music and also provides a podcast feed for updates.
Tags: roundup